The futuristic energy grids comprise of predominantly renewable generation, to align with the sustainable development goals. This would require integration of renewable energy sources at different levels of the power system out of which, consumers turning into power producers, often referred to as prosumers is an important aspect. Prosumers who generate excess power beyond self-consumption […]
Read More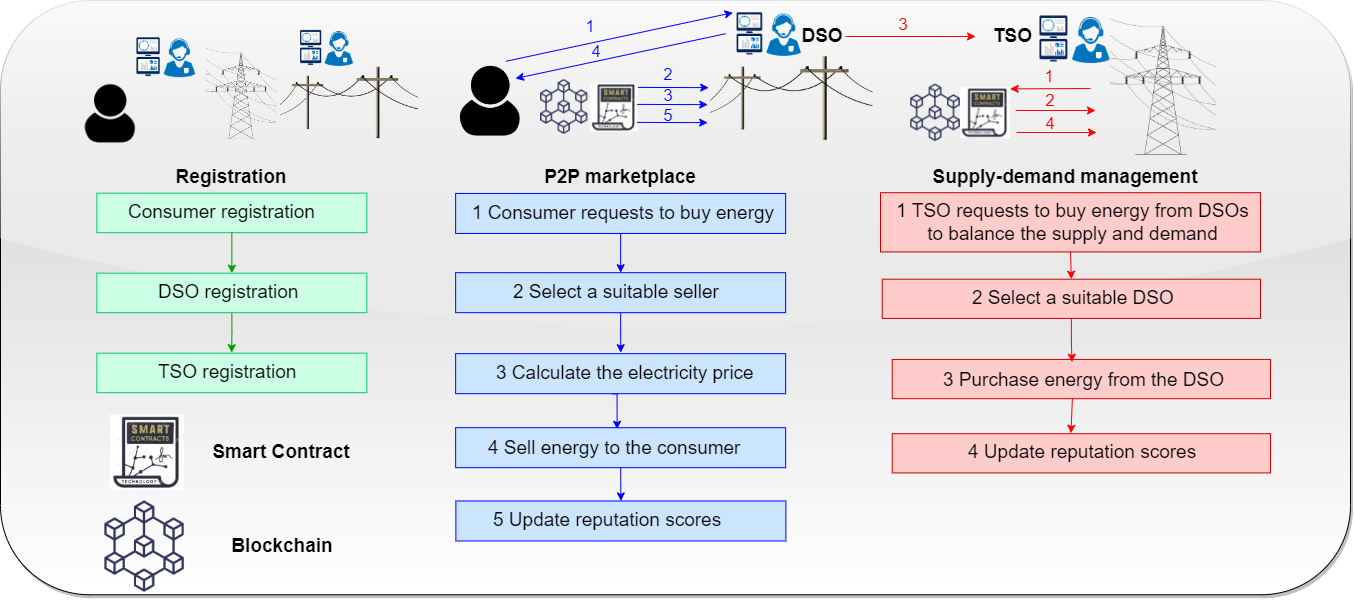
Utilization of a Blockchain-based Reputation Management System for Energy Trading in SmartGrid 2.0
- January 21, 2024
- Comments off