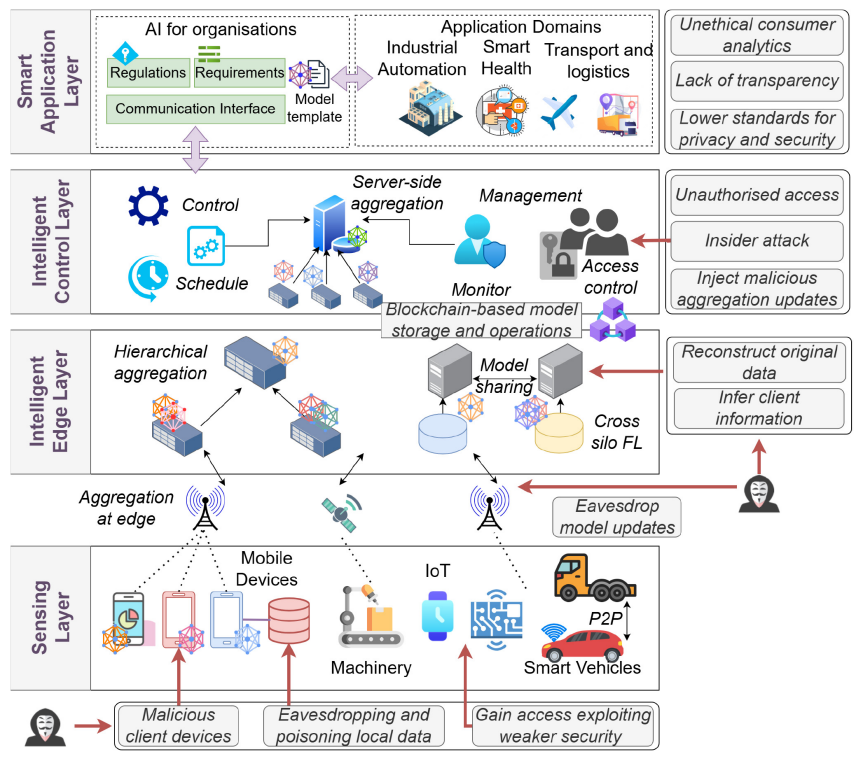
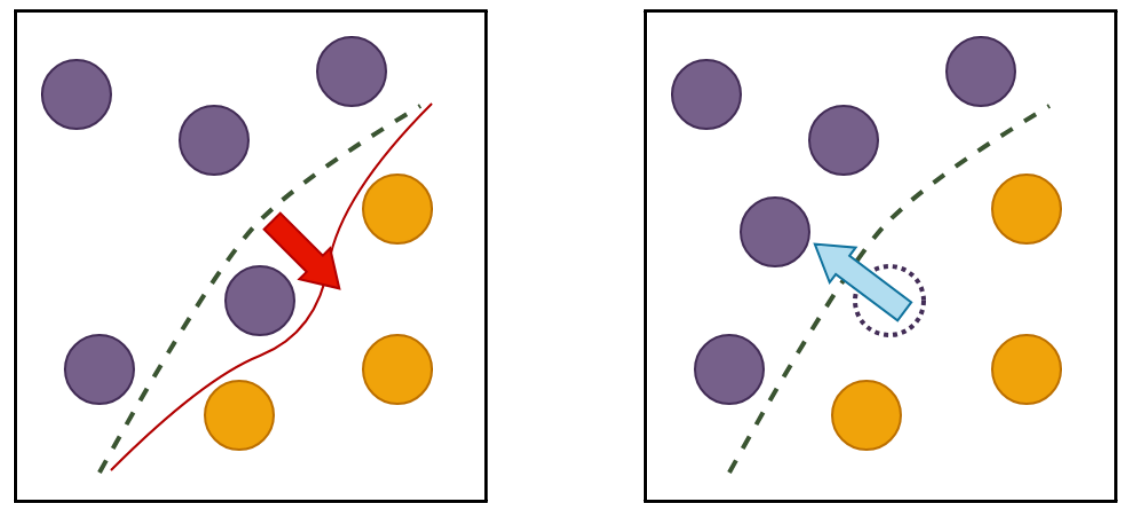
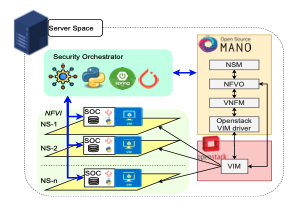
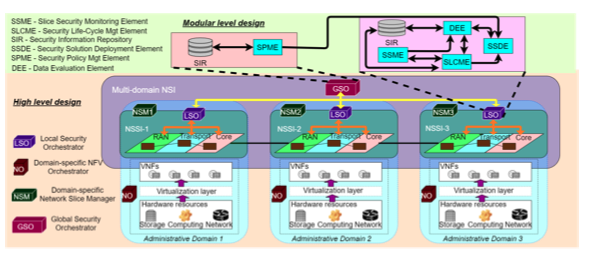
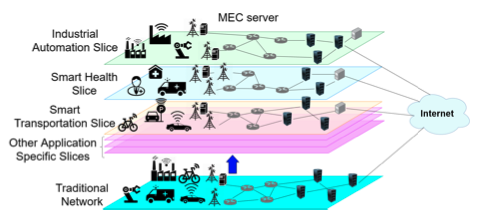
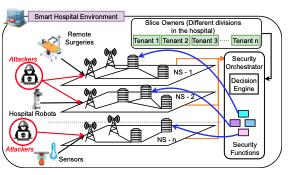
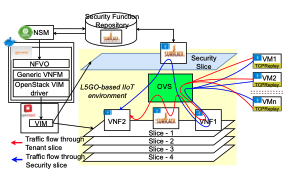
On March 12, 2025, the Cyber Ireland Dublin Chapter, in collaboration with the UCD School of Computer Science and the Advance Centre – Professional Education for Digital Transformation, hosted an insightful Industry & Academia Meeting at University College Dublin. The event brought together leading experts to explore how AI can enhance security across the software […]
Read More