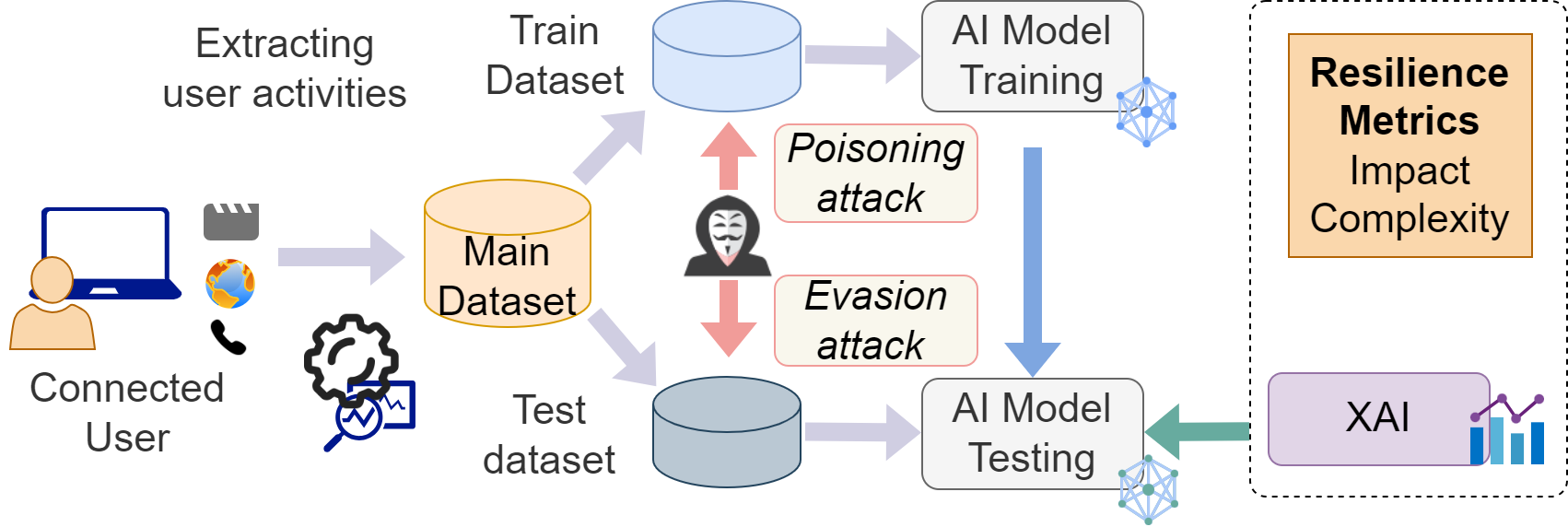
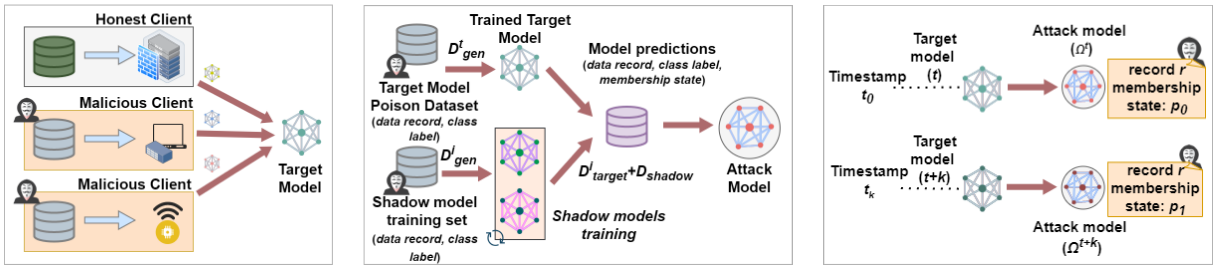
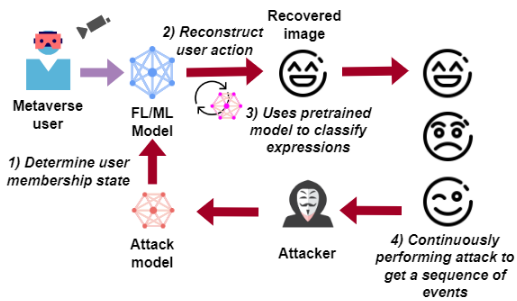
An emergence of attention and regulations on consumer privacy can be observed over the recent years with the ubiquitous availability of IoT systems handling personal data. Federated Learning (FL) arises as a privacy-preserved Machine Learning (ML) technique where data can be kept private within these devices without transmitting to third parties. Yet, many privacy attacks […]
Read More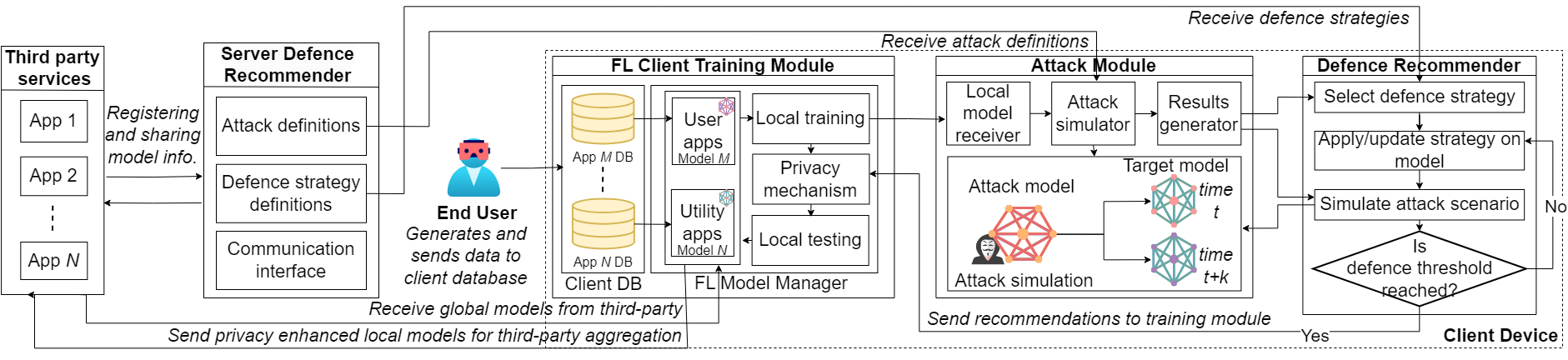
Rec-Def: A Recommendation-based Defence Mechanism for Privacy Preservation in Federated Learning Systems
- November 19, 2023
- Comments off