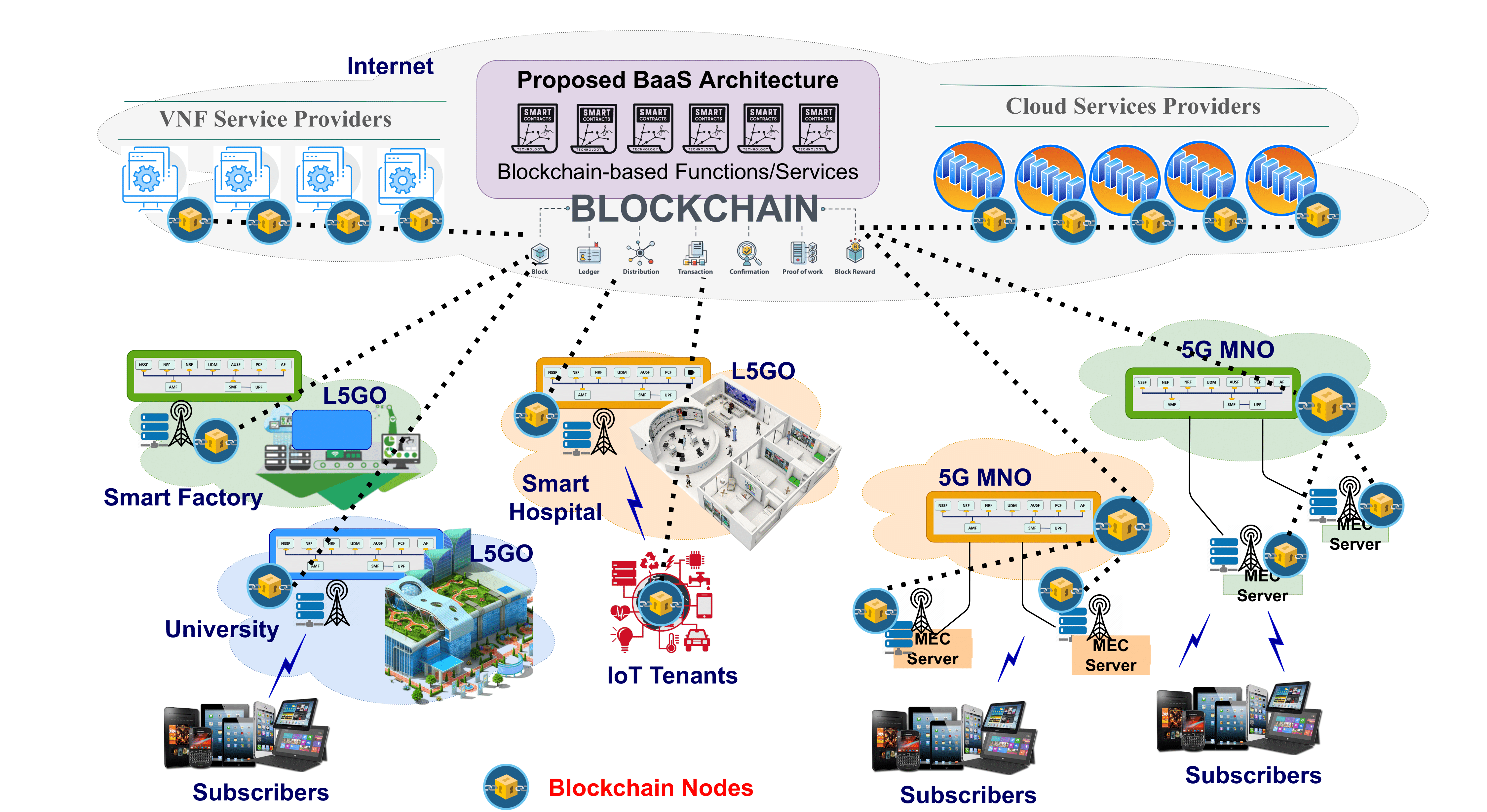
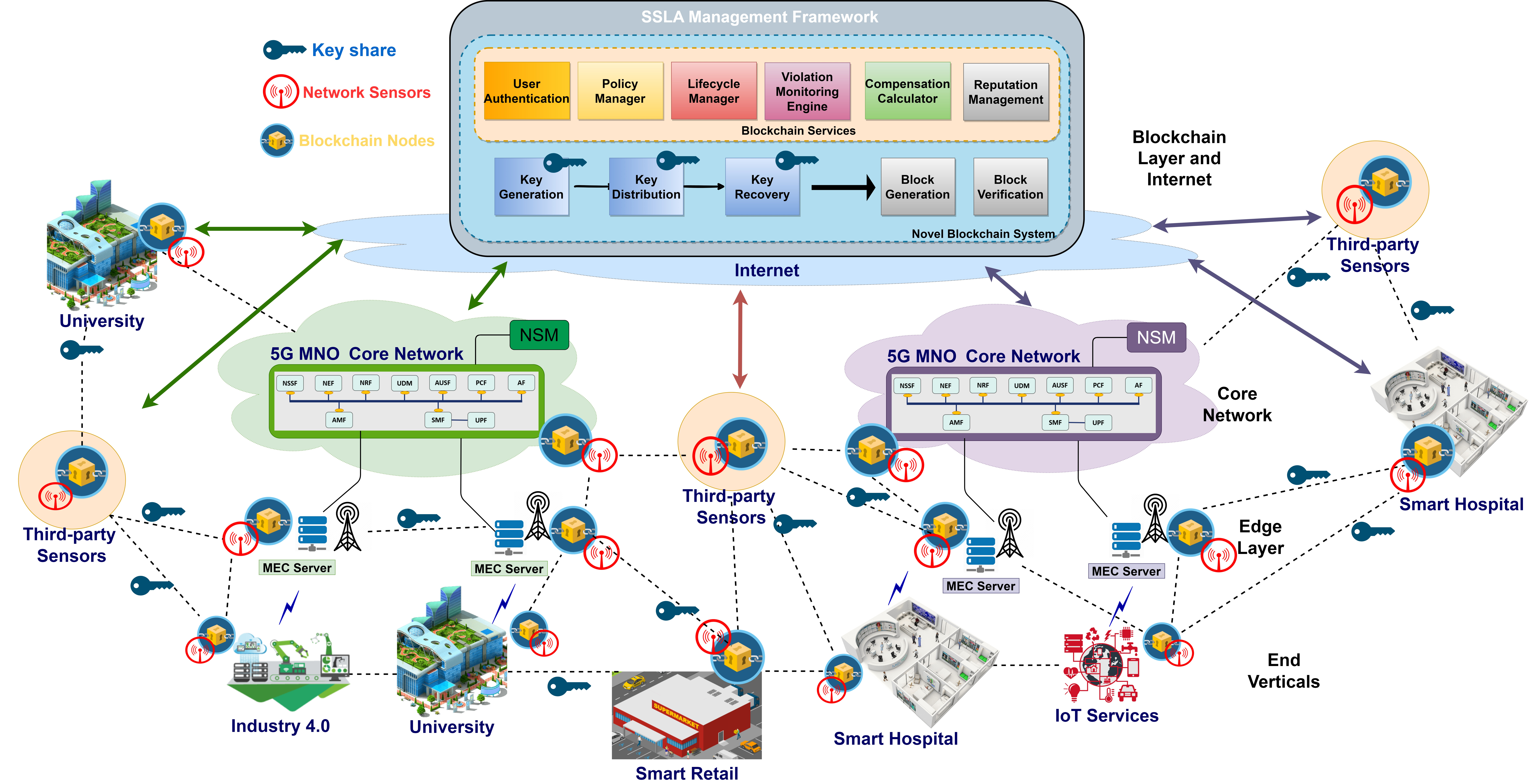
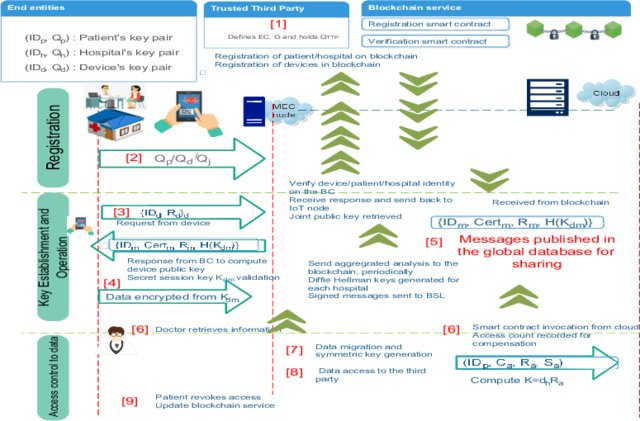
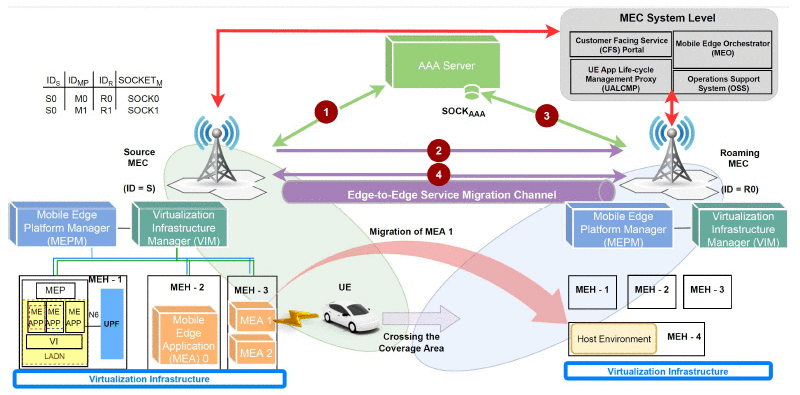
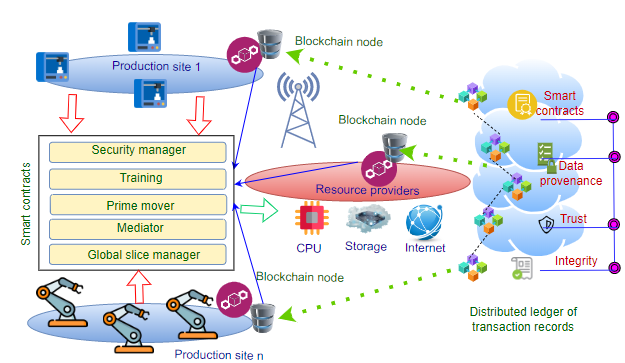
Local 5G Operator (L5GO) concept is one of themost prominent versatile applications of the 5G in the nearfuture. The popularity of L5GOs will trigger a greater numberof roaming and offloading events between mobile operators.However, existing static and operator-assisted roaming andoffloading procedures are inefficient for the L5GO ecosystem due topoor service quality, data privacy issues, data […]
Read More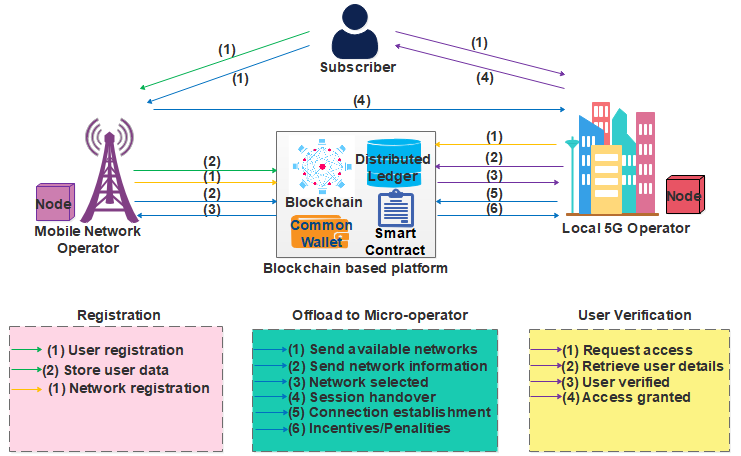
Blockchain-based Roaming and Offload Service Platform for Local 5G Operators
- February 1, 2023
- Comments off