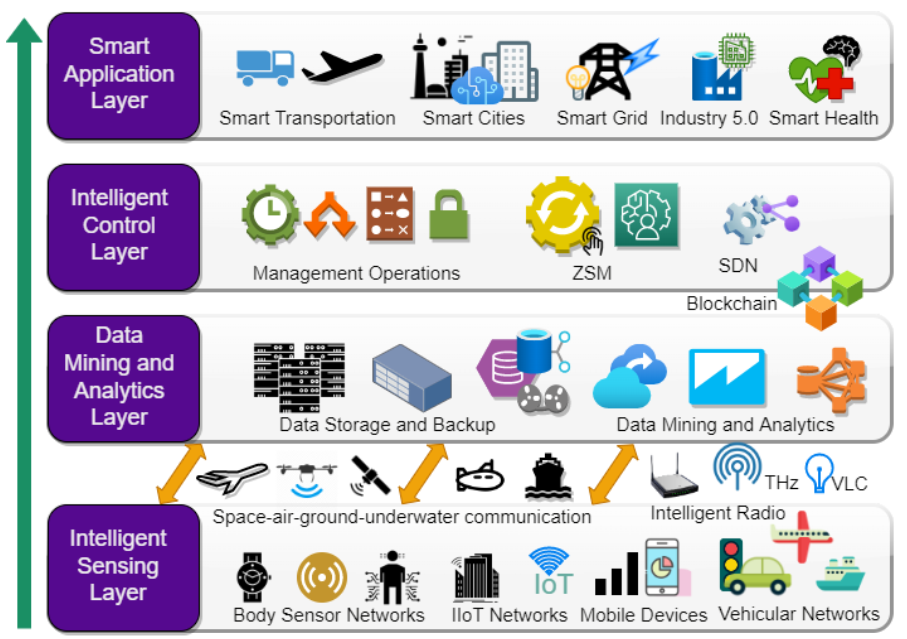
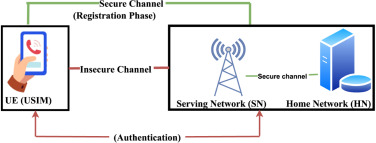
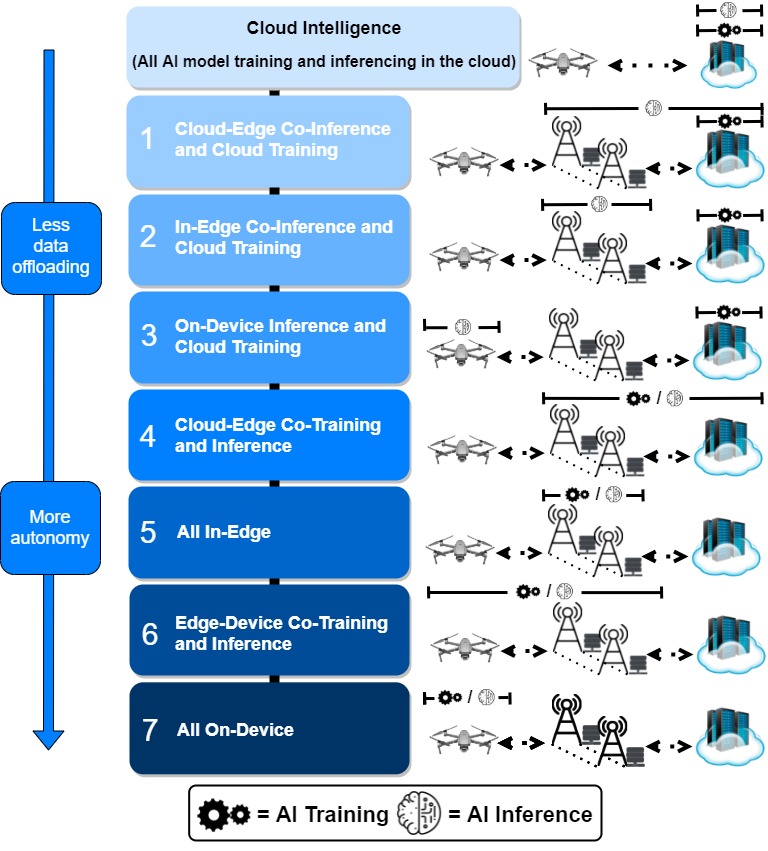
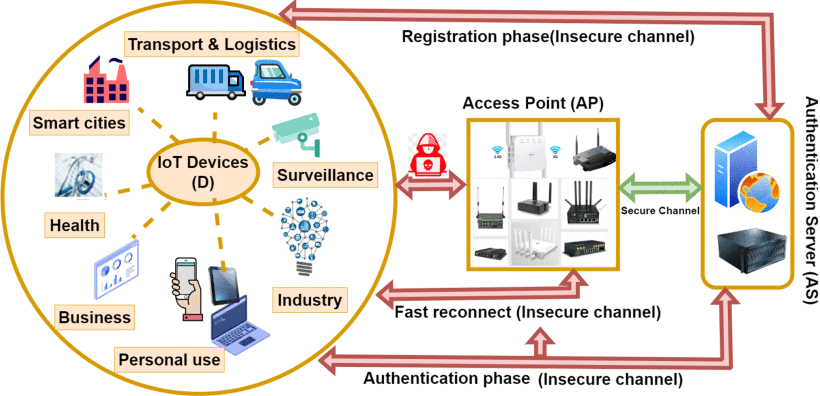
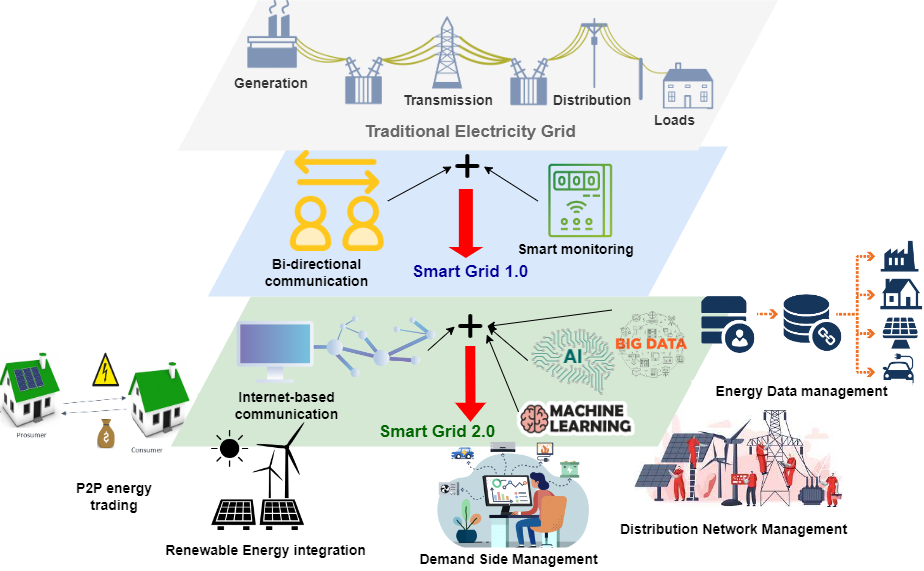
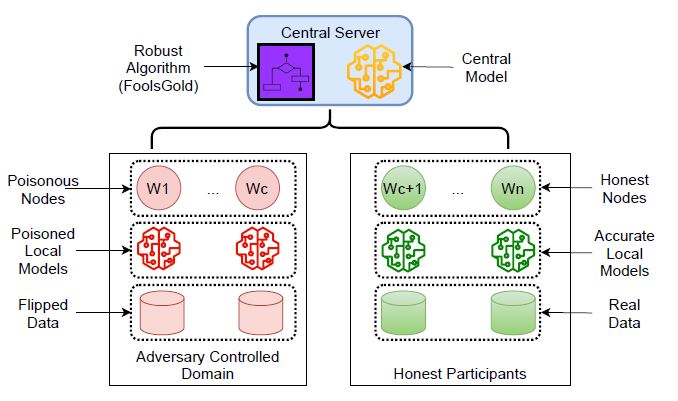
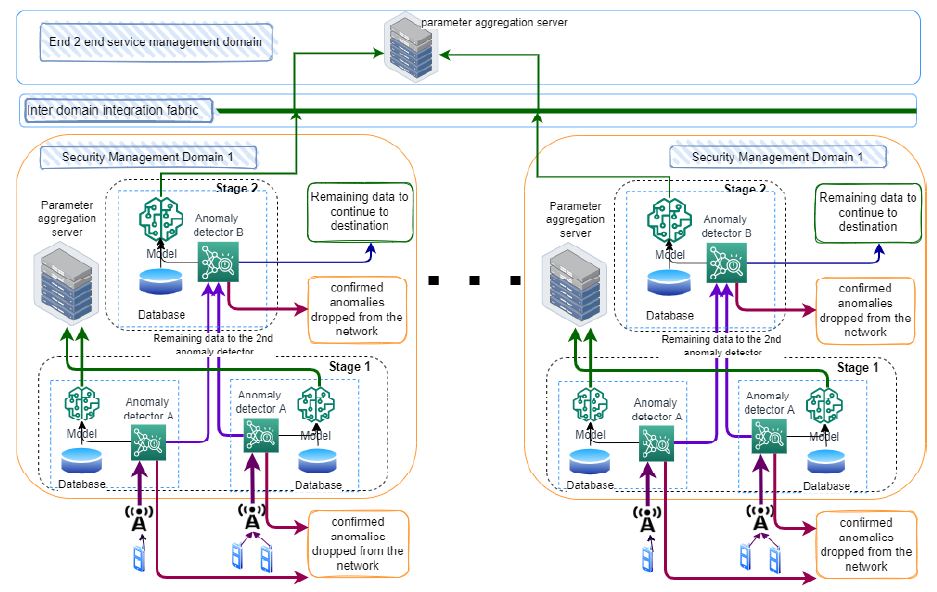
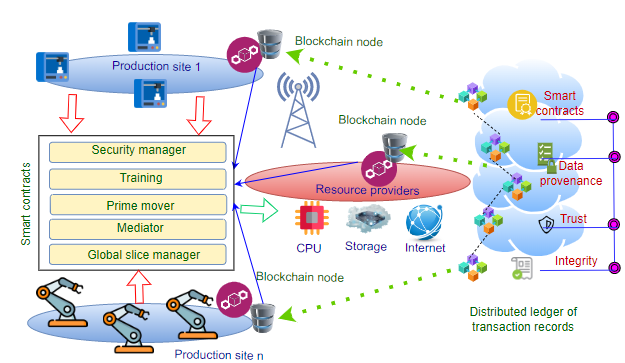
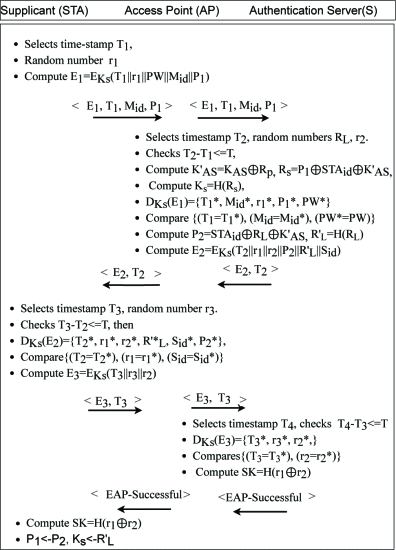
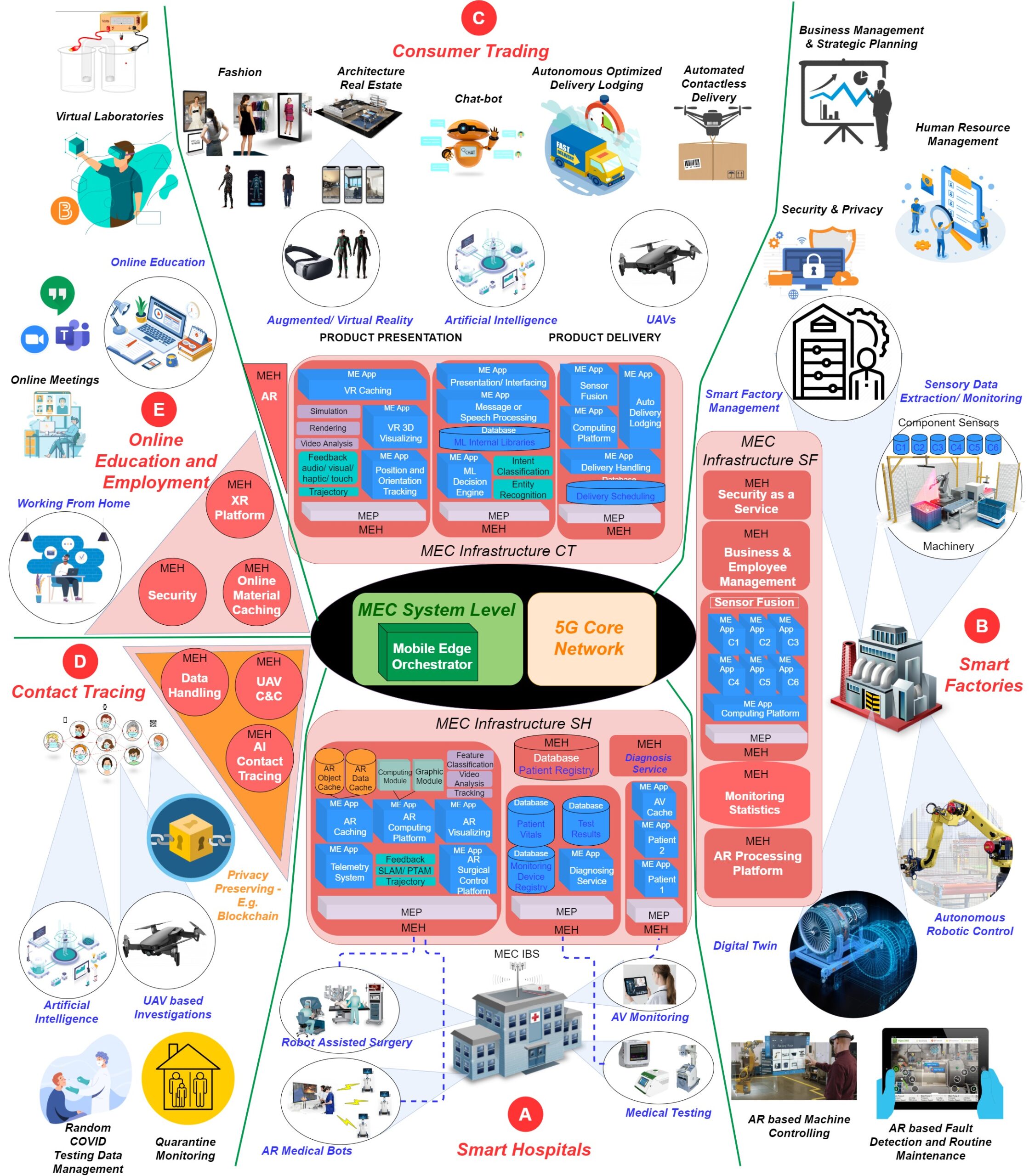
Massive developments in mobile wireless telecommunication networks have been made during the last few decades. At present, mobile users are getting familiar with the latest 5G networks, and the discussion for the next generation of Beyond 5G (B5G)/6G networks has already been initiated. It is expected that B5G/6G will push the existing network capabilities to […]
Read More