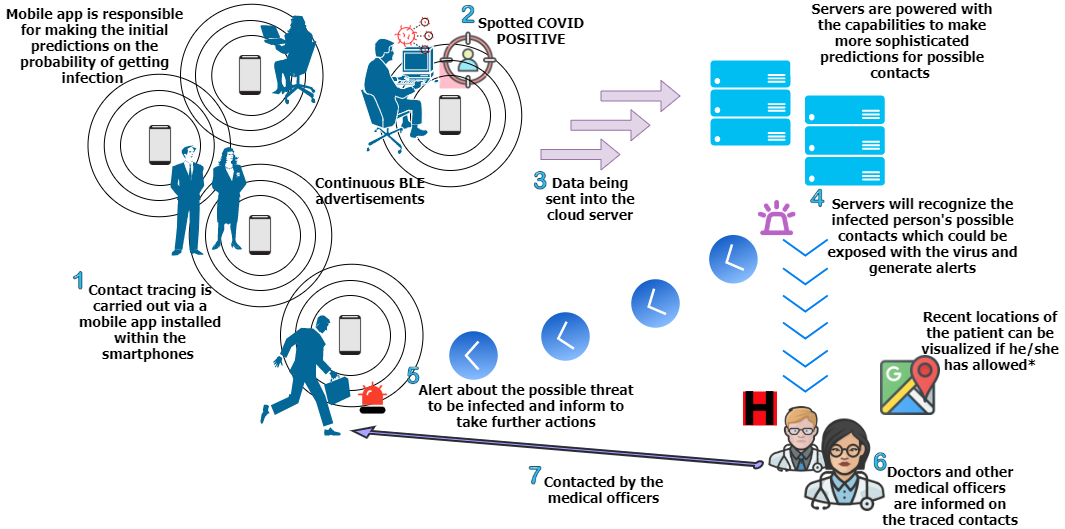
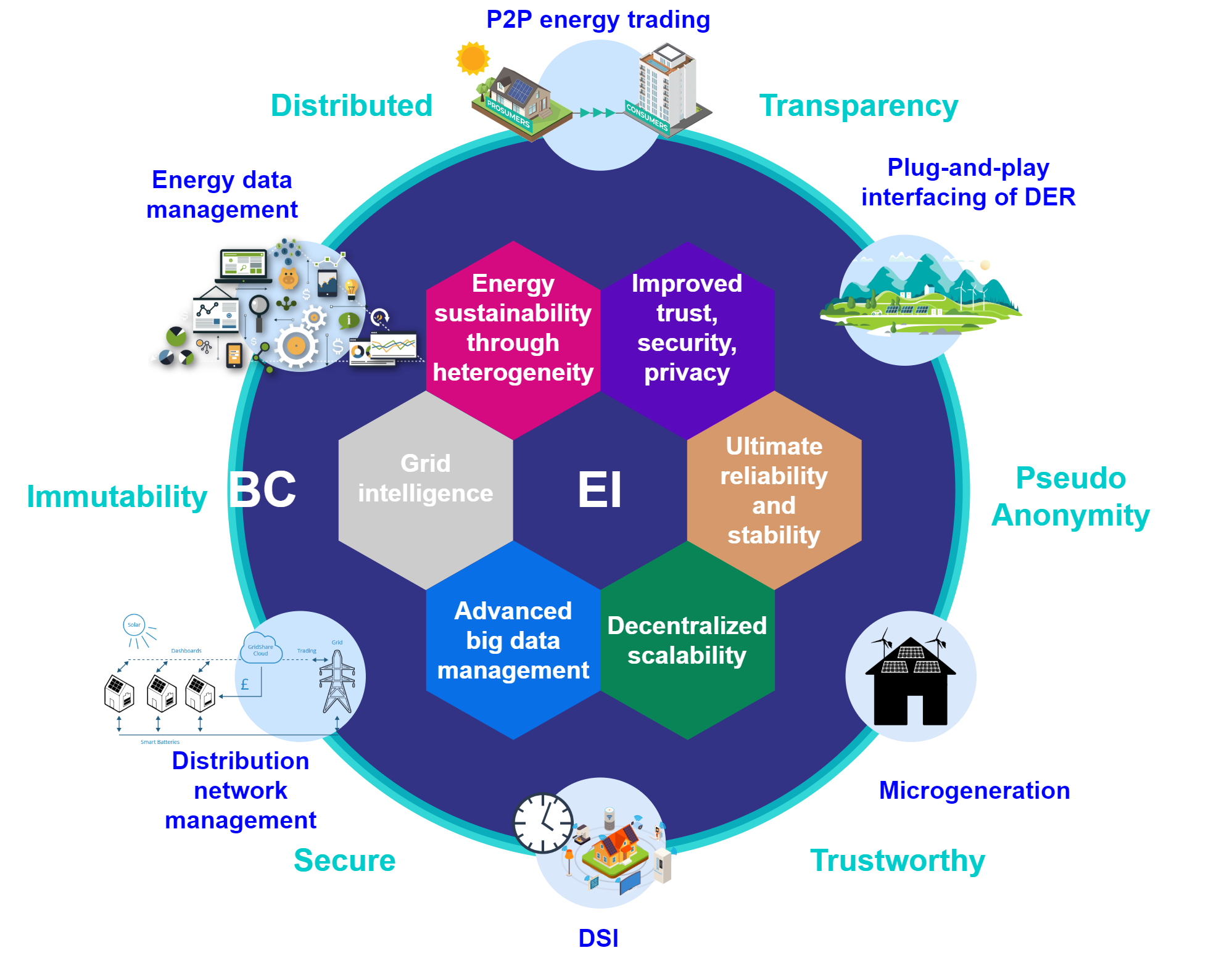
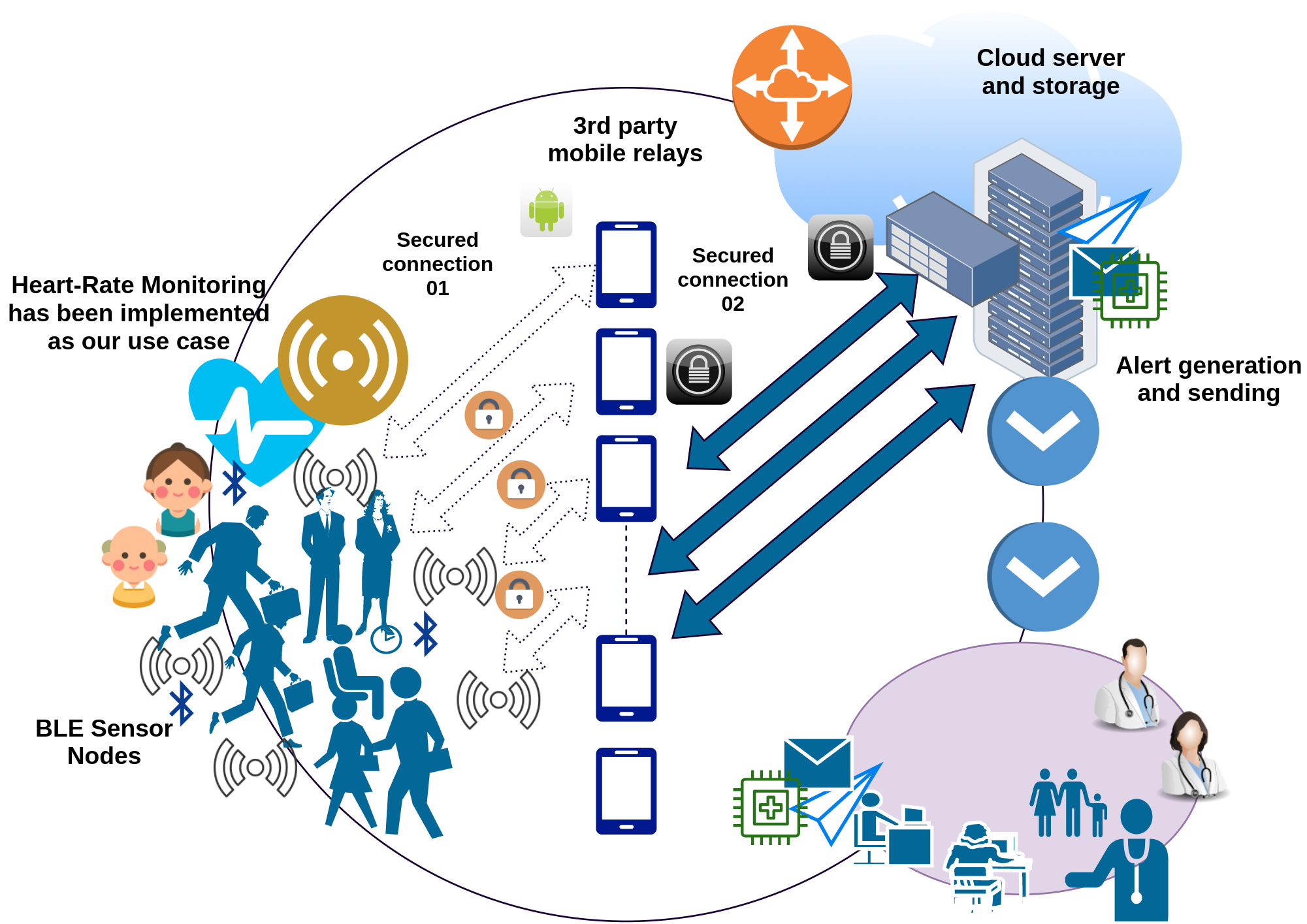
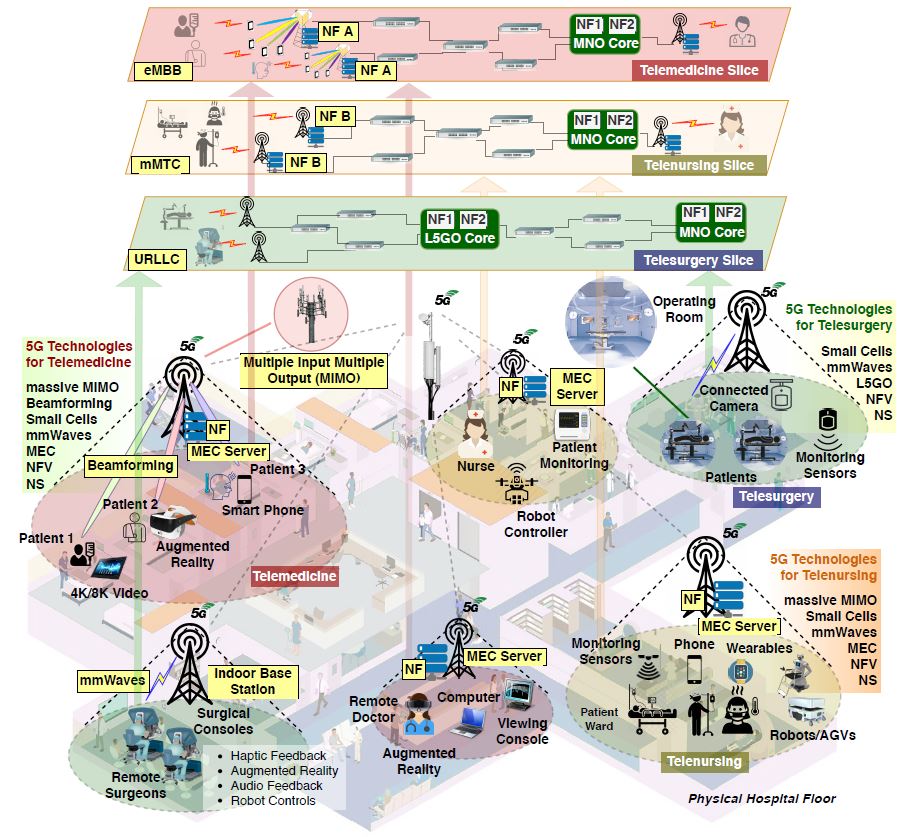
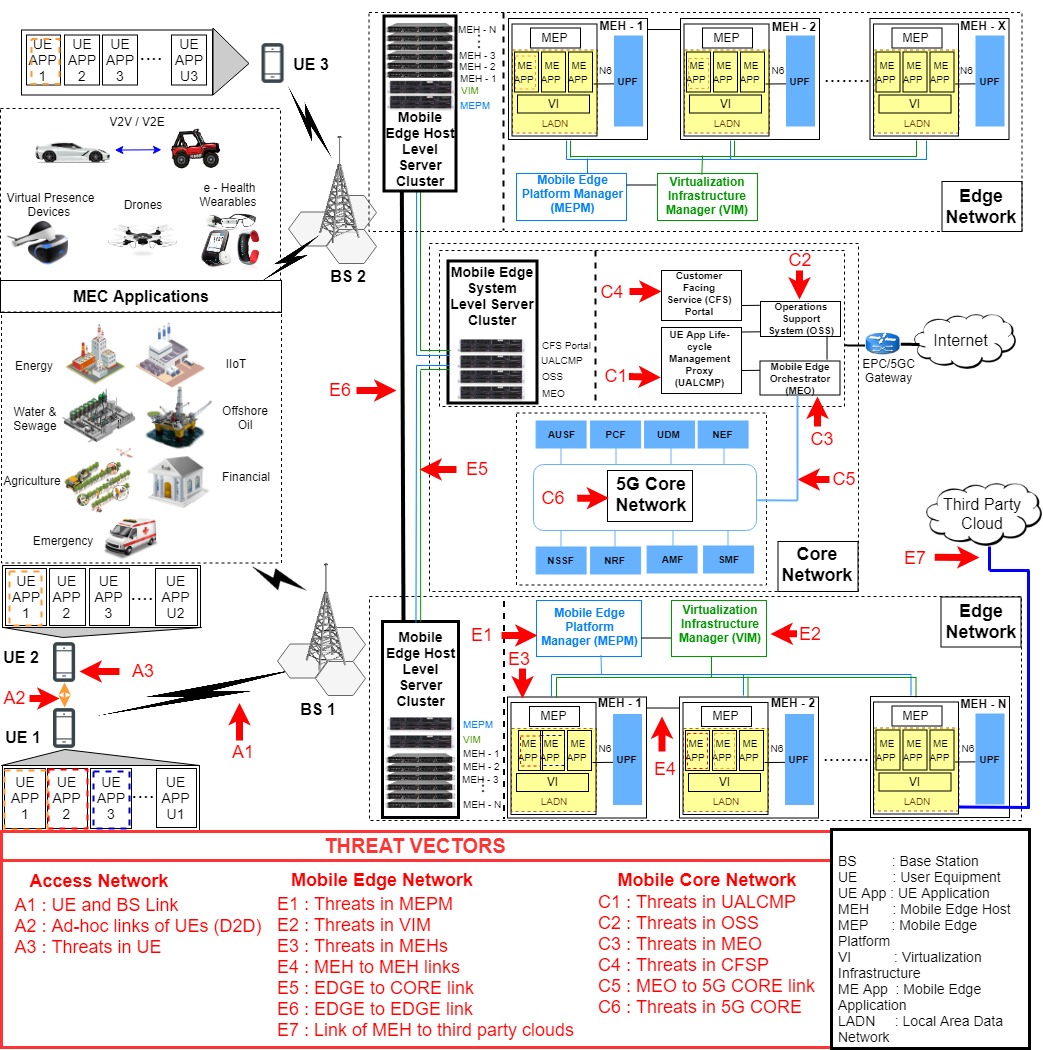
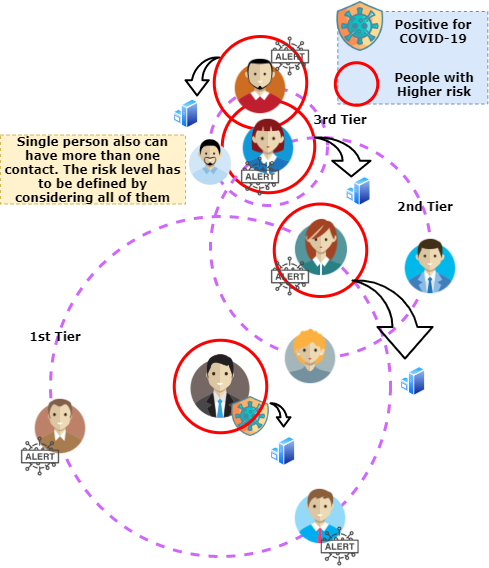
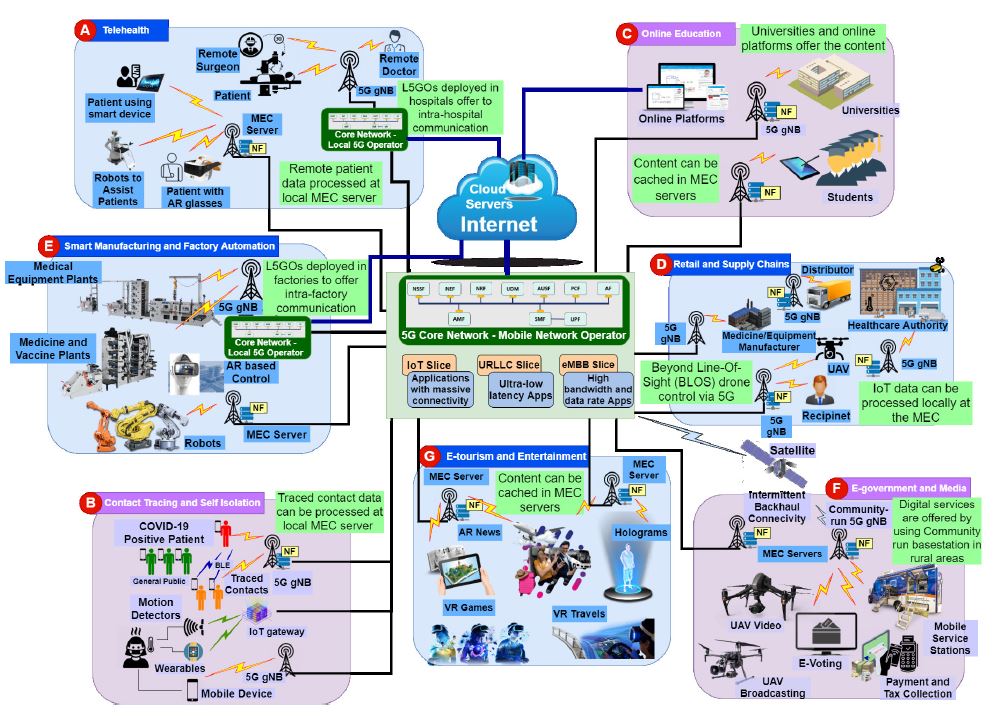
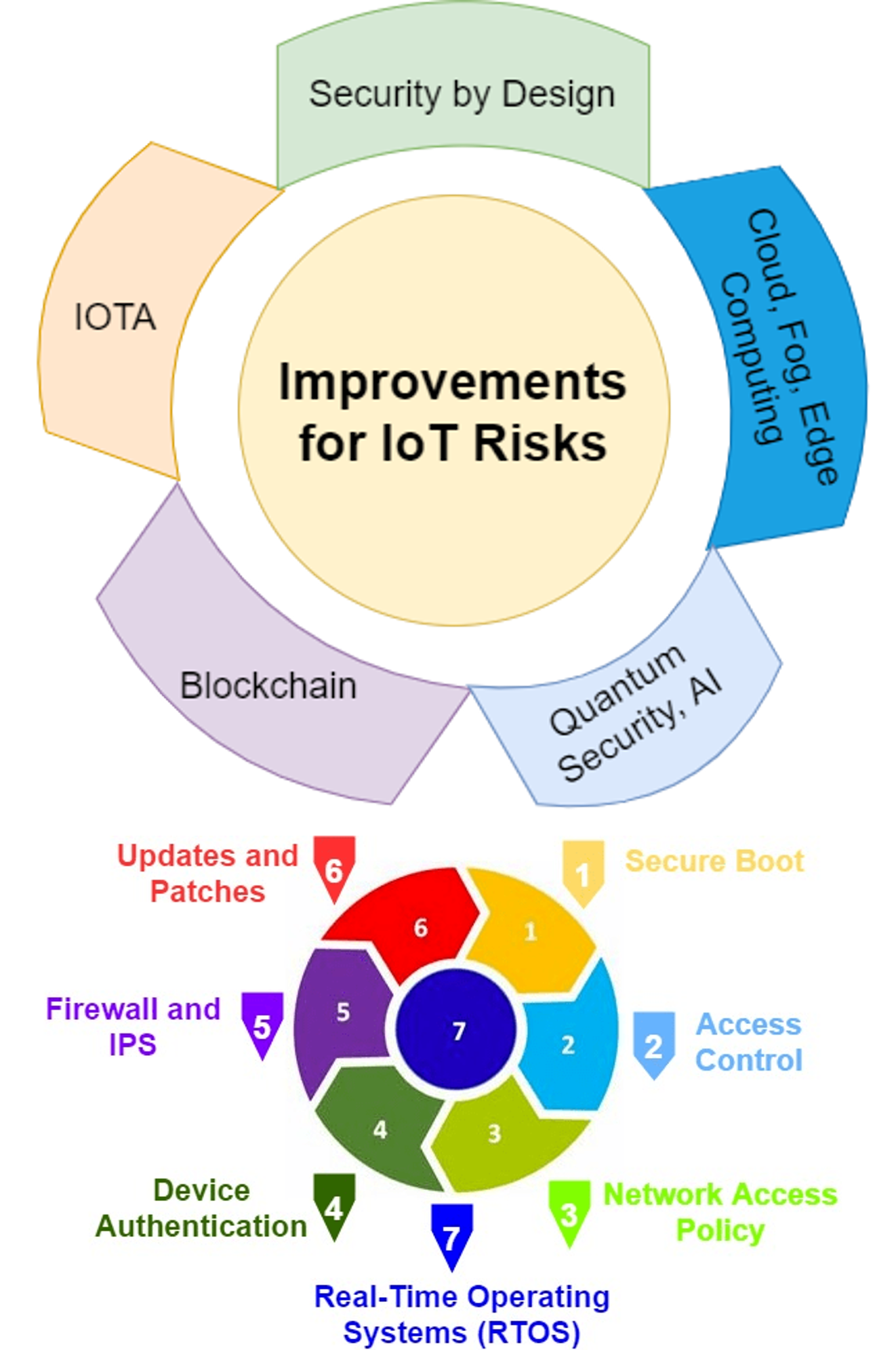
The entire world progression has ceased with the unexpected outbreak of the COVID-19 pandemic, and urges the requirement for contact-less and autonomous services and applications. Realizing these predominantly Internet of Things (IoT) based applications demands a holistic pervasive computinginfrastructure. In this paper, we conduct a survey to determine the possible pervasive approaches for utilizing the […]
Read More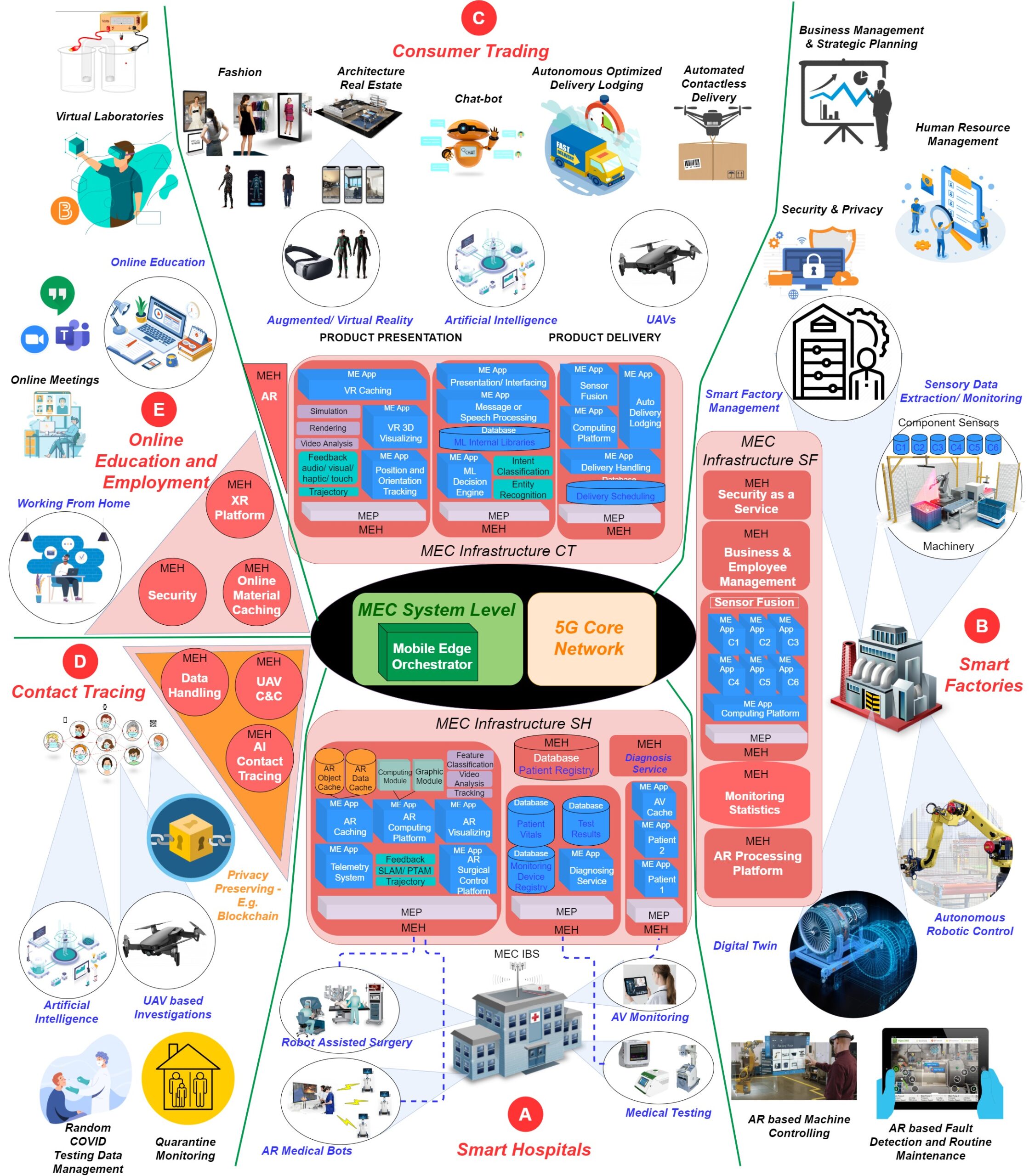
Realizing Contact-less Applications with Multi-Access Edge Computing
- March 10, 2022
- Comments off