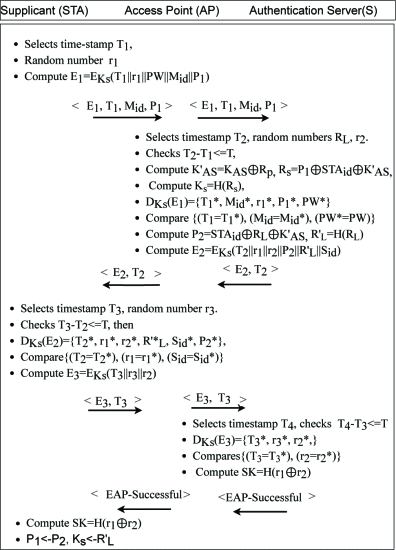
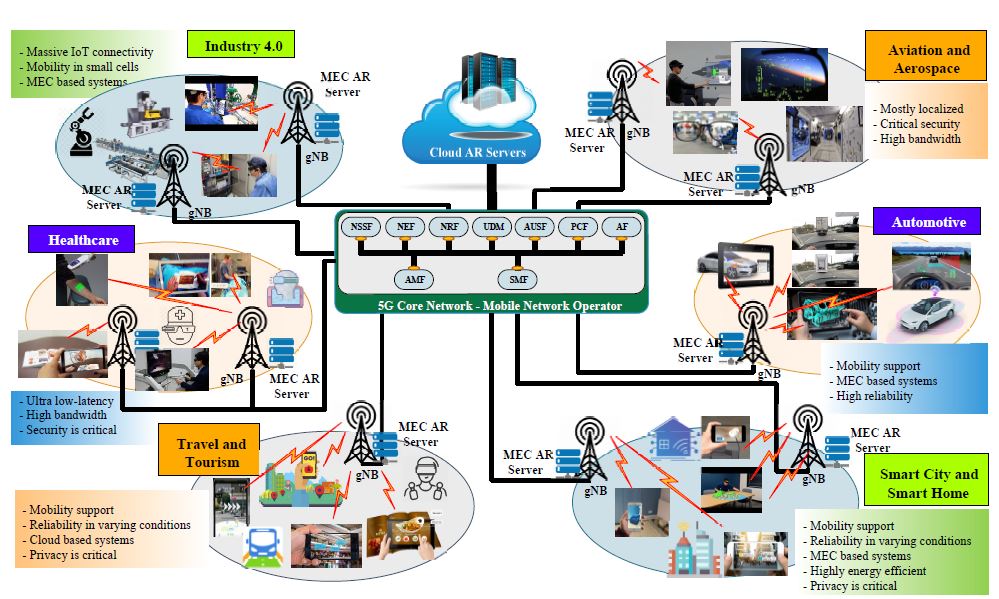
One of the primary authentication mechanisms defined for the 5G system is the 5G-Authentication and Key Agreement (5G-AKA) protocol. It is set to be used in the next generation of mobile communications but has several serious flaws such as privacy issues, vulnerability to traceability attacks, and has de-synchronization problem. To deal with these issues, An Braeken presented […]
Read More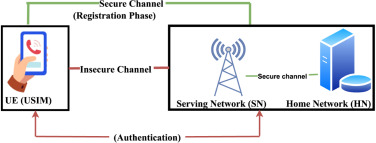
An improved and provably secure symmetric-key based 5G-AKA Protocol
- September 12, 2022
- Comments off