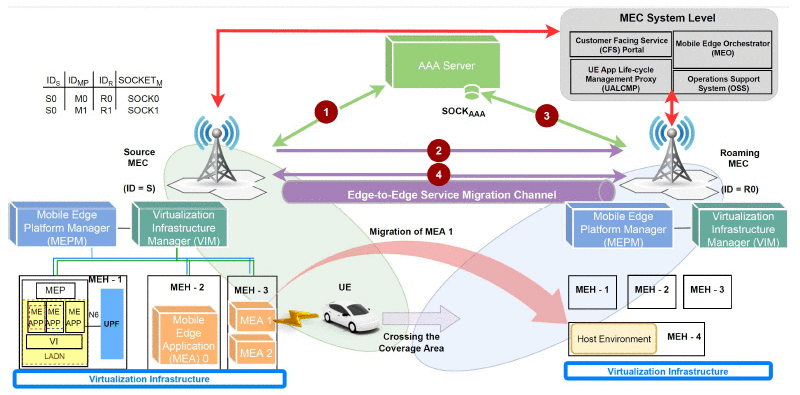
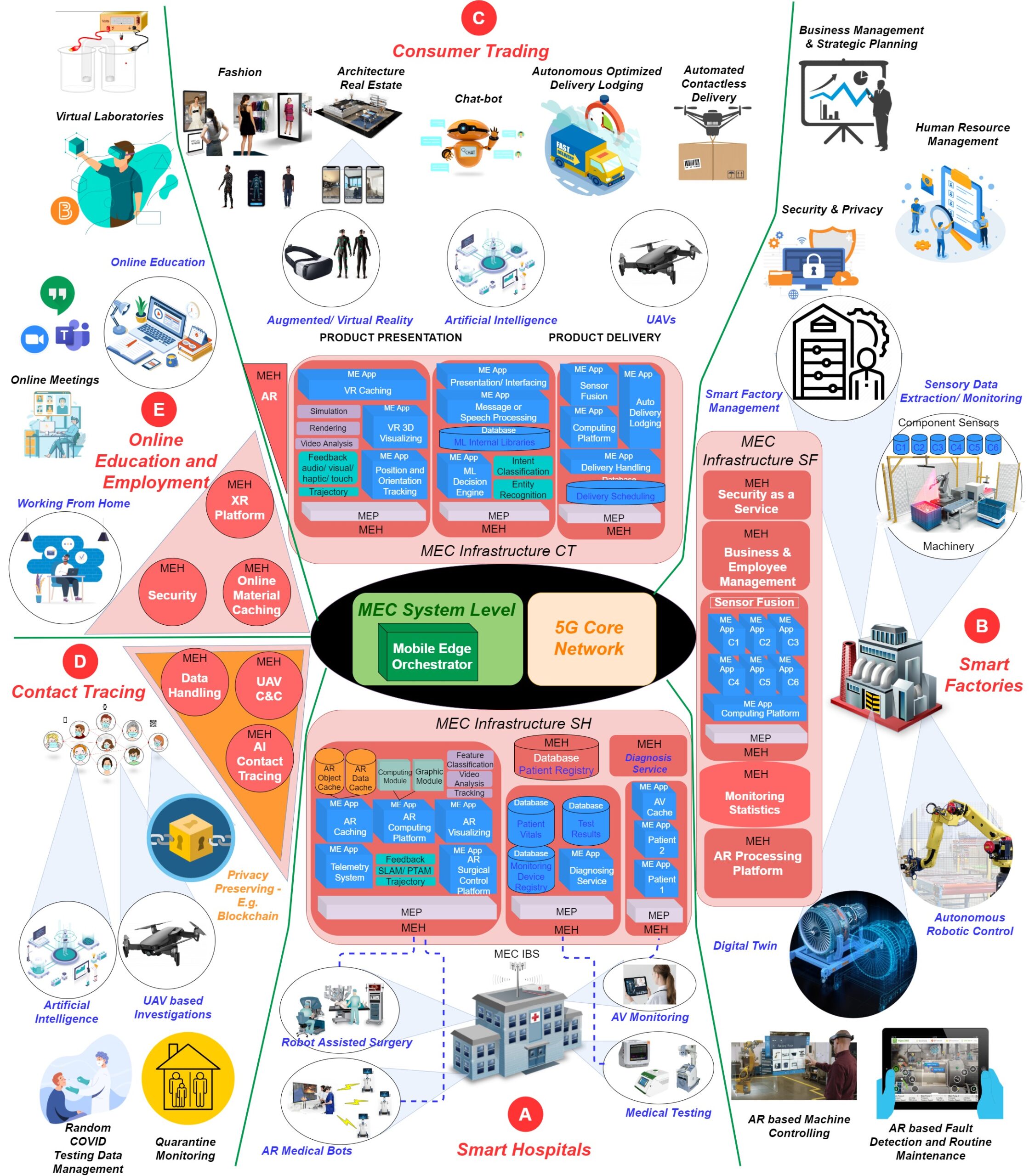
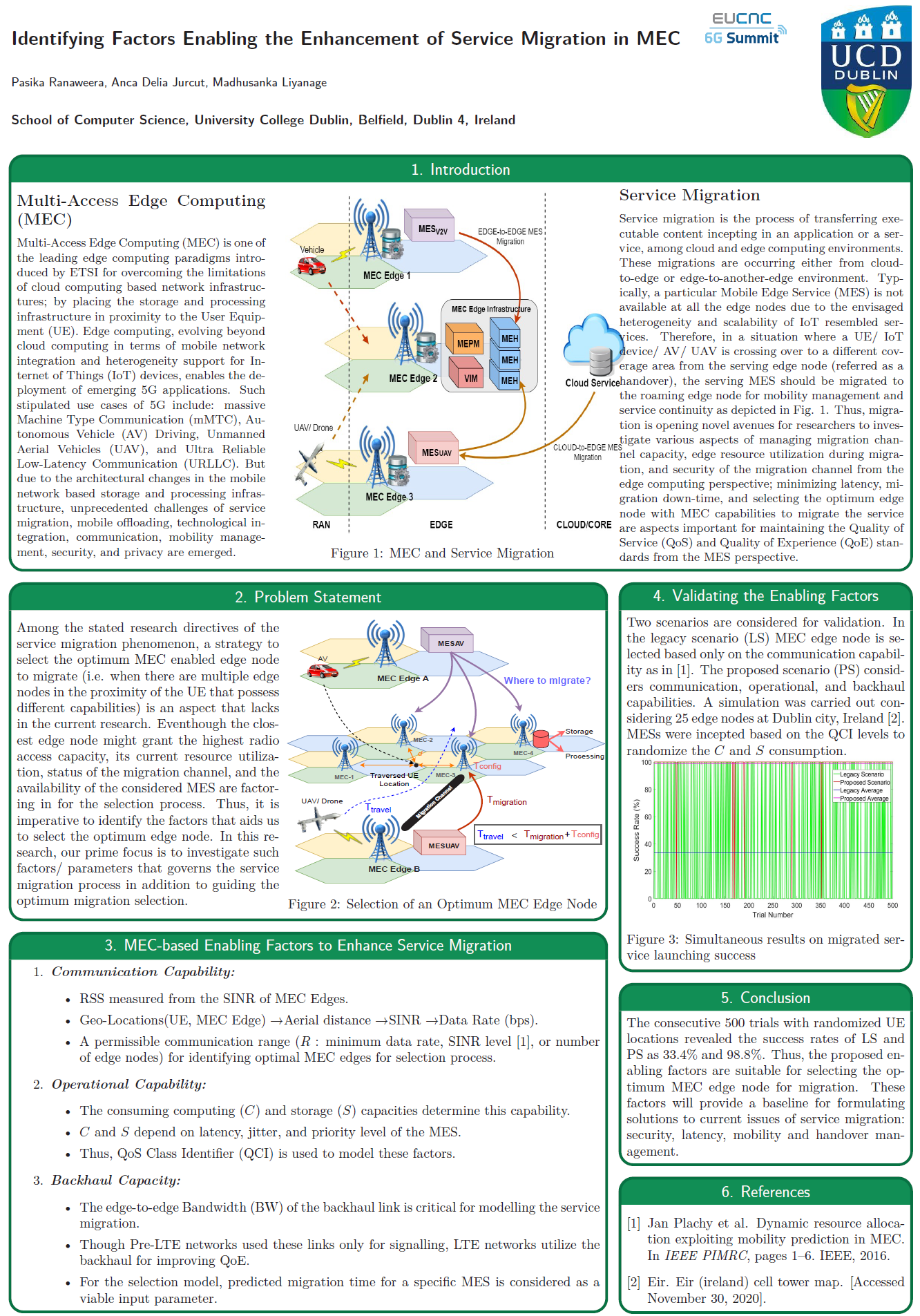
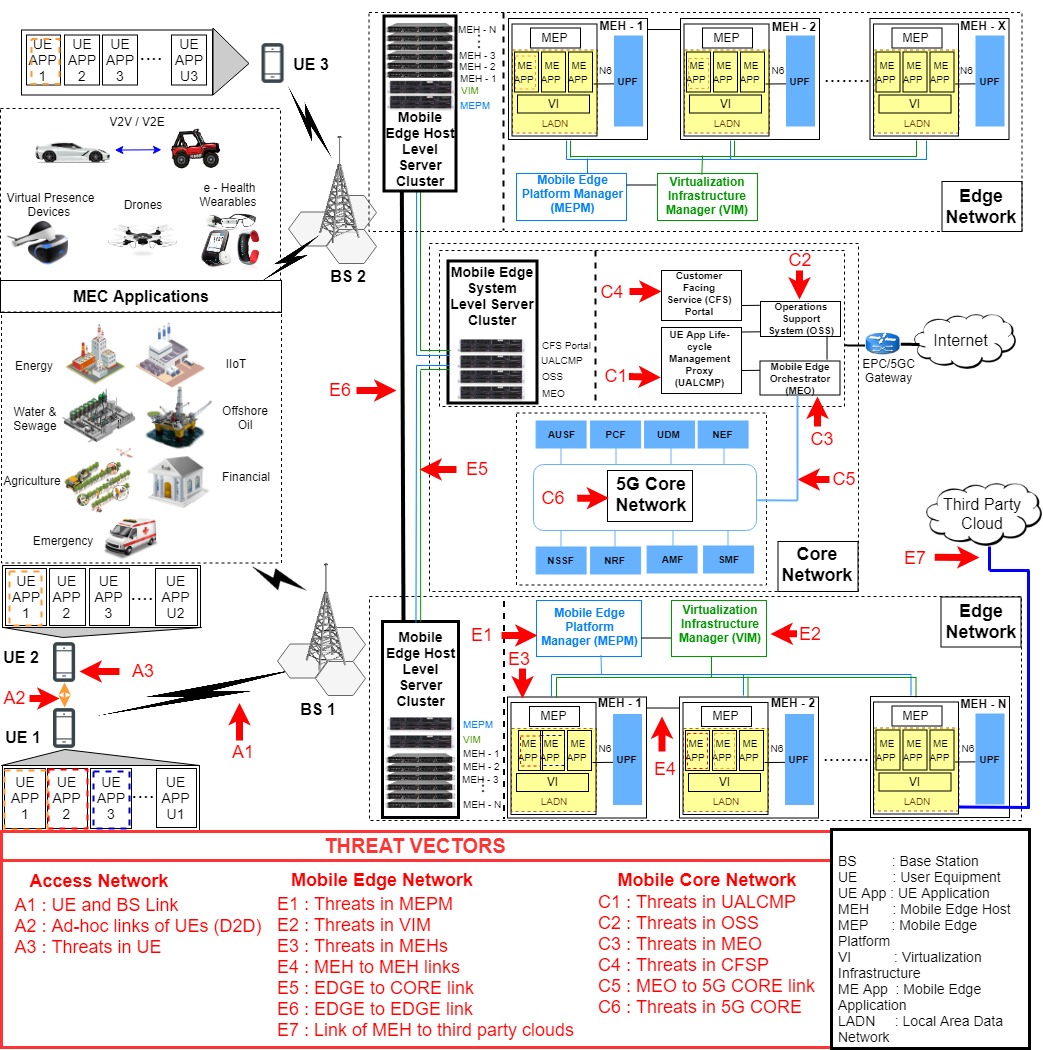
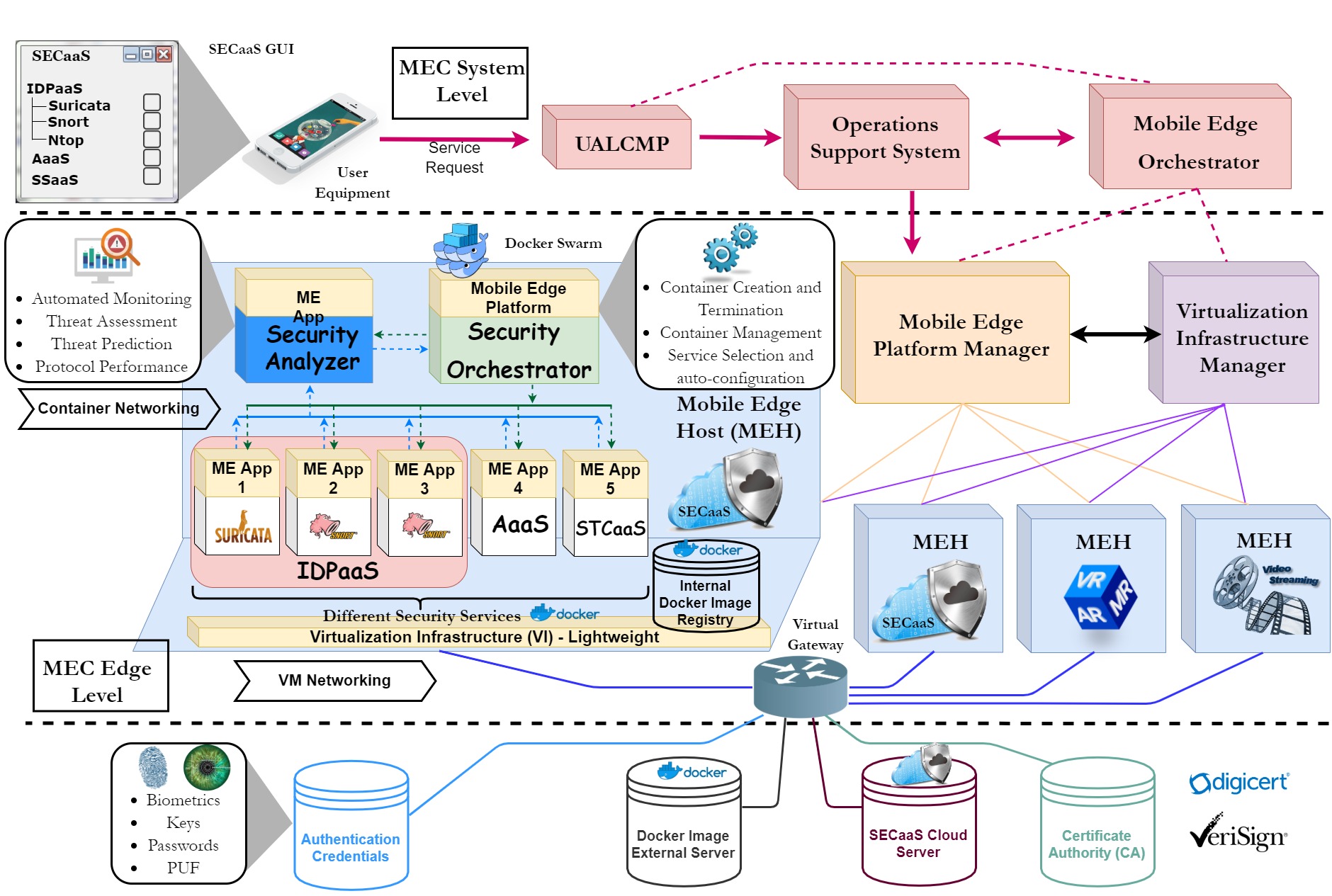
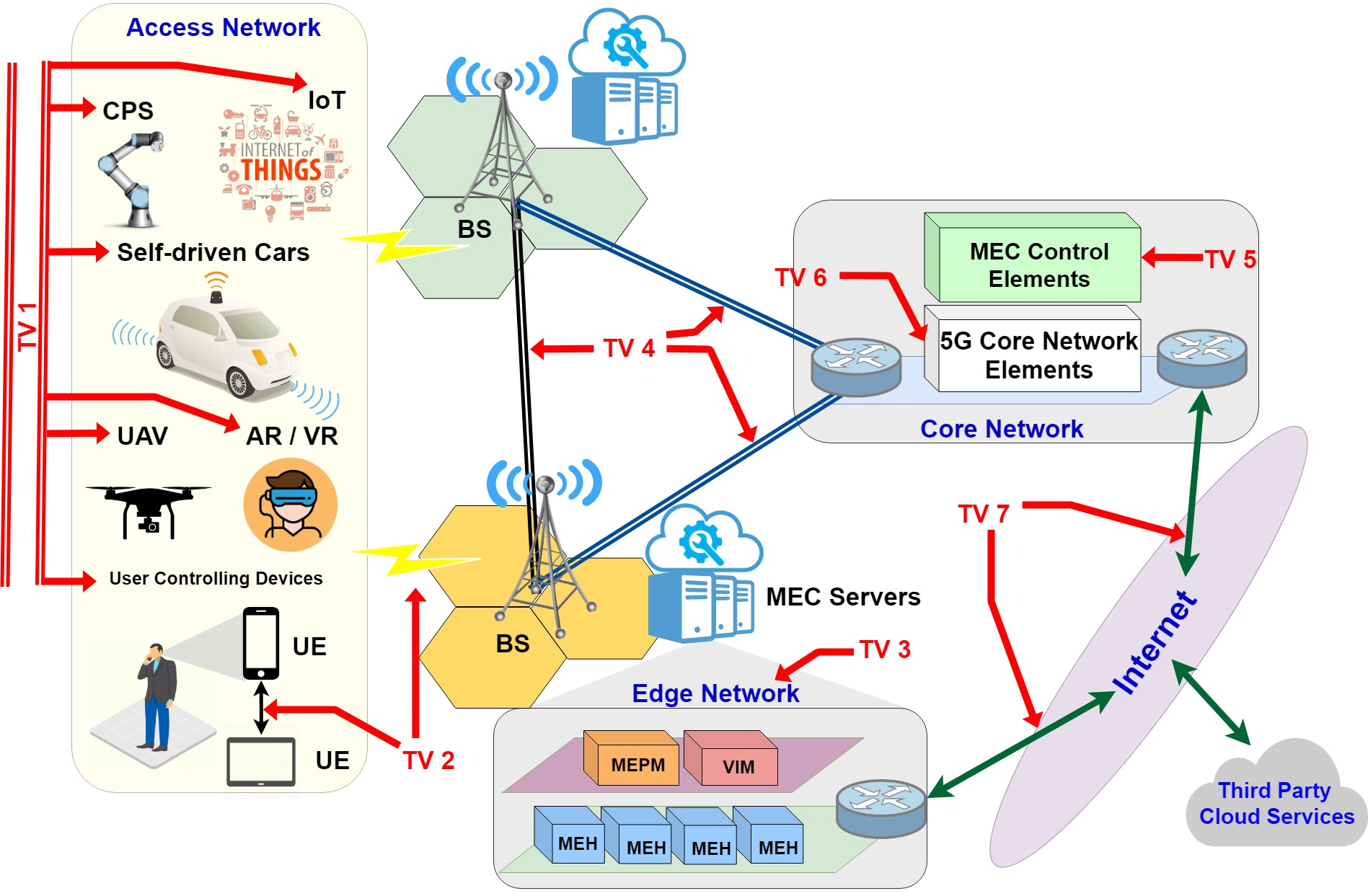
Edge computing paradigms were an expedient innovation for elevating the contemporary standards of mobile and Internet networks. As specified in Multi-Access Edge Computing (MEC) standardization, edge computing serviceable infrastructures are running on virtualization technologies to provide dynamic and flexible service instances. Since the inception and operation of the services are executing at the edge level […]
Read MoreService Migration Authentication Protocol for MEC
- December 7, 2022
- Comments off
Multi-Access Edge Computing (MEC) is a novel edge computing paradigm that enhances the access level capacity of mobile networks by shifting the serviceable Data center infrastructure proximate to the end devices. With this proximate placement and service provisioning, migration of a service from one edge enabled gNodeB (gNB) to another is intrinsic to maintain the […]
Read More