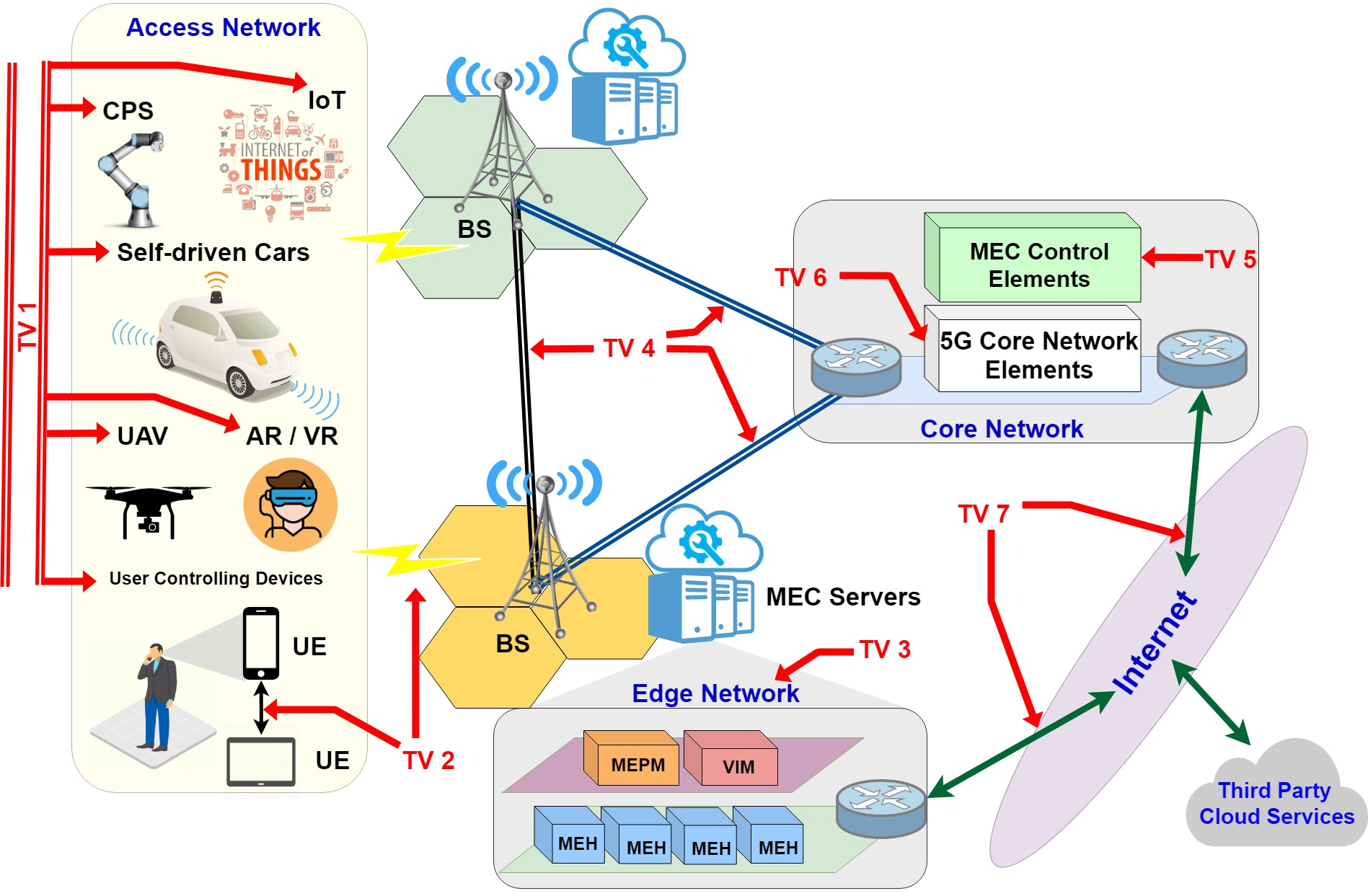
The European Telecommunications Standards Institute (ETSI) has introduced the paradigm of Multi-Access Edge Computing (MEC) to enable efficient and fast data processing in mobile networks. Among other technological requirements, security and privacy are significant factors in the realization of MECdeployments. In this paper, we analyse the security and privacy of the MEC system. We introduce […]
Read More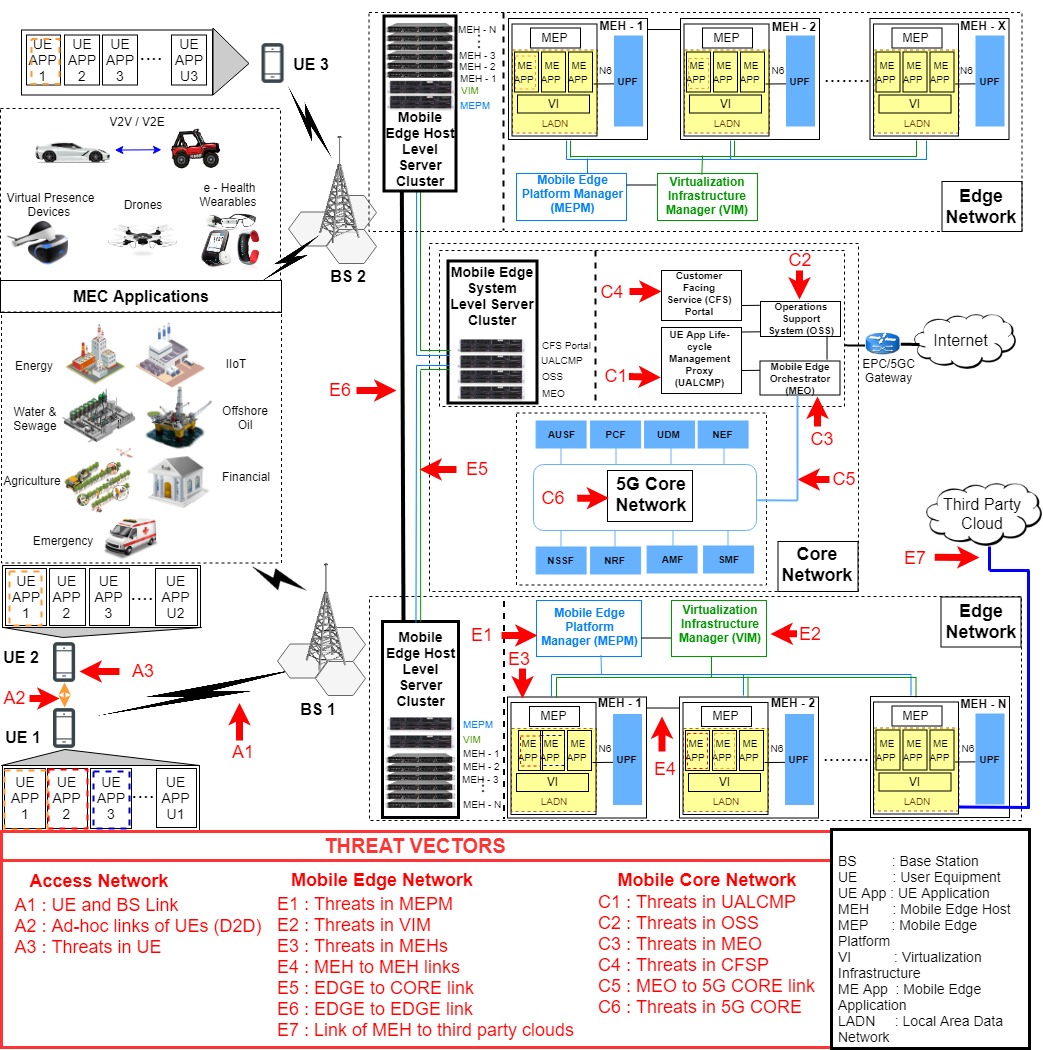
Survey on Multi-Access Edge Computing Security and Privacy
- February 26, 2021
- Comments off