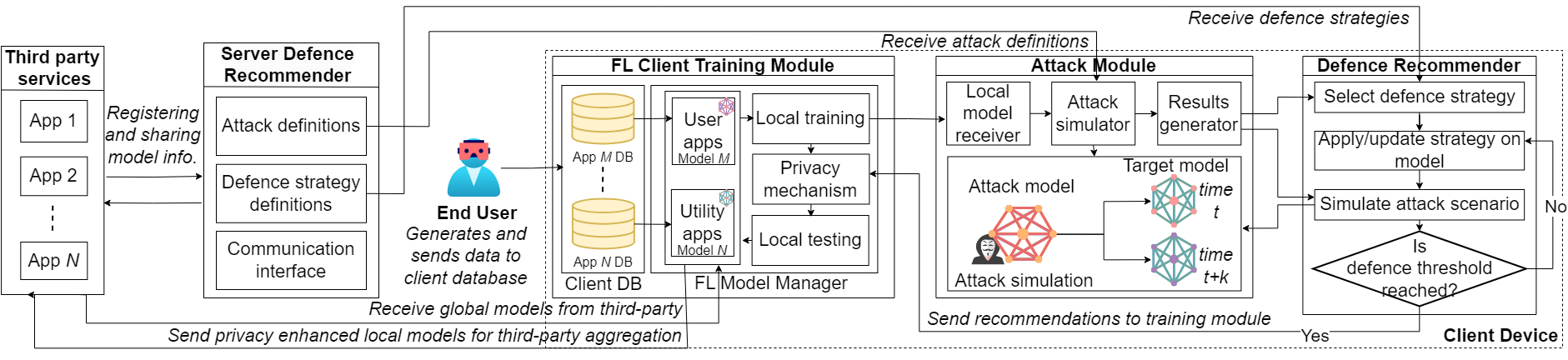
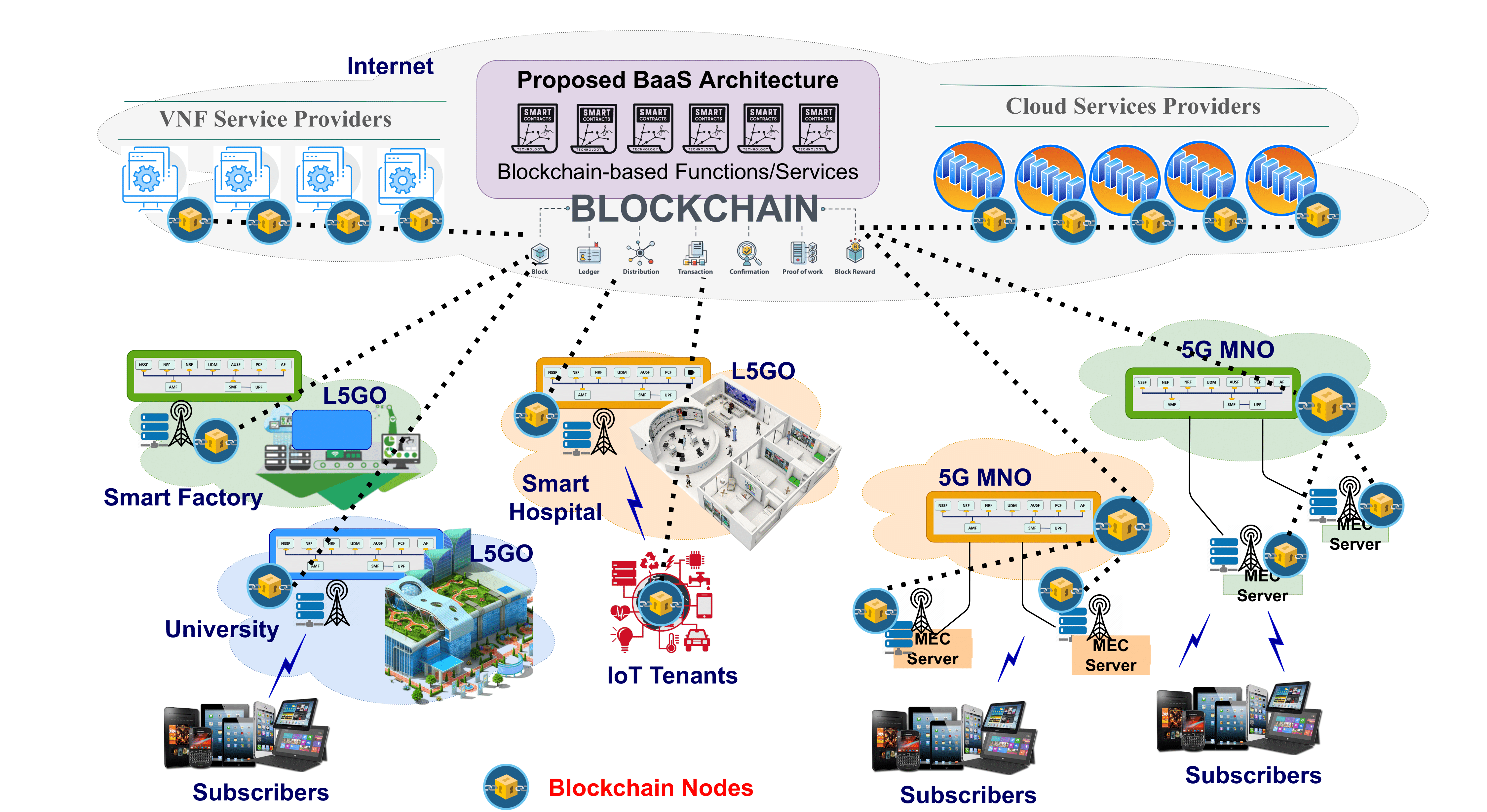
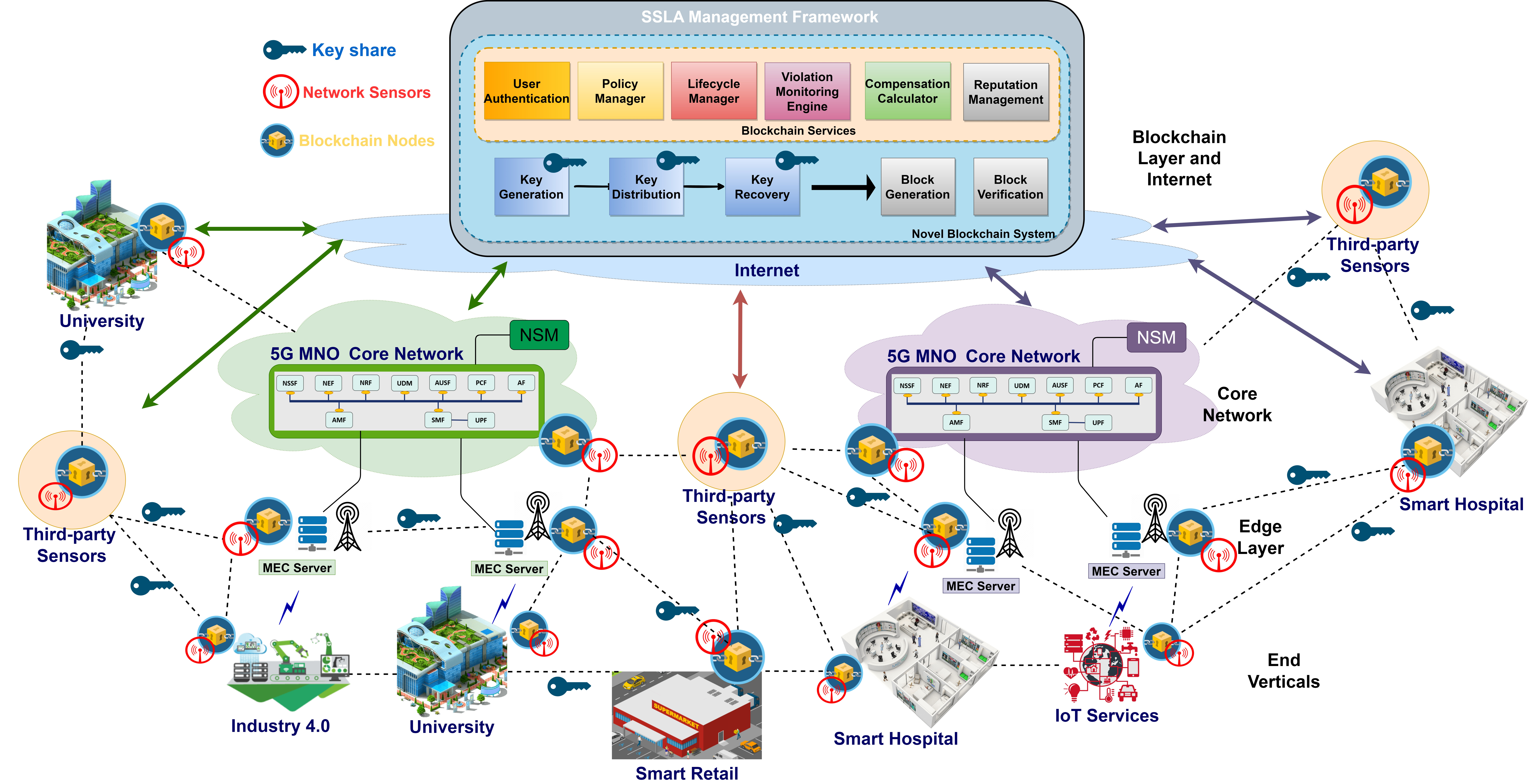
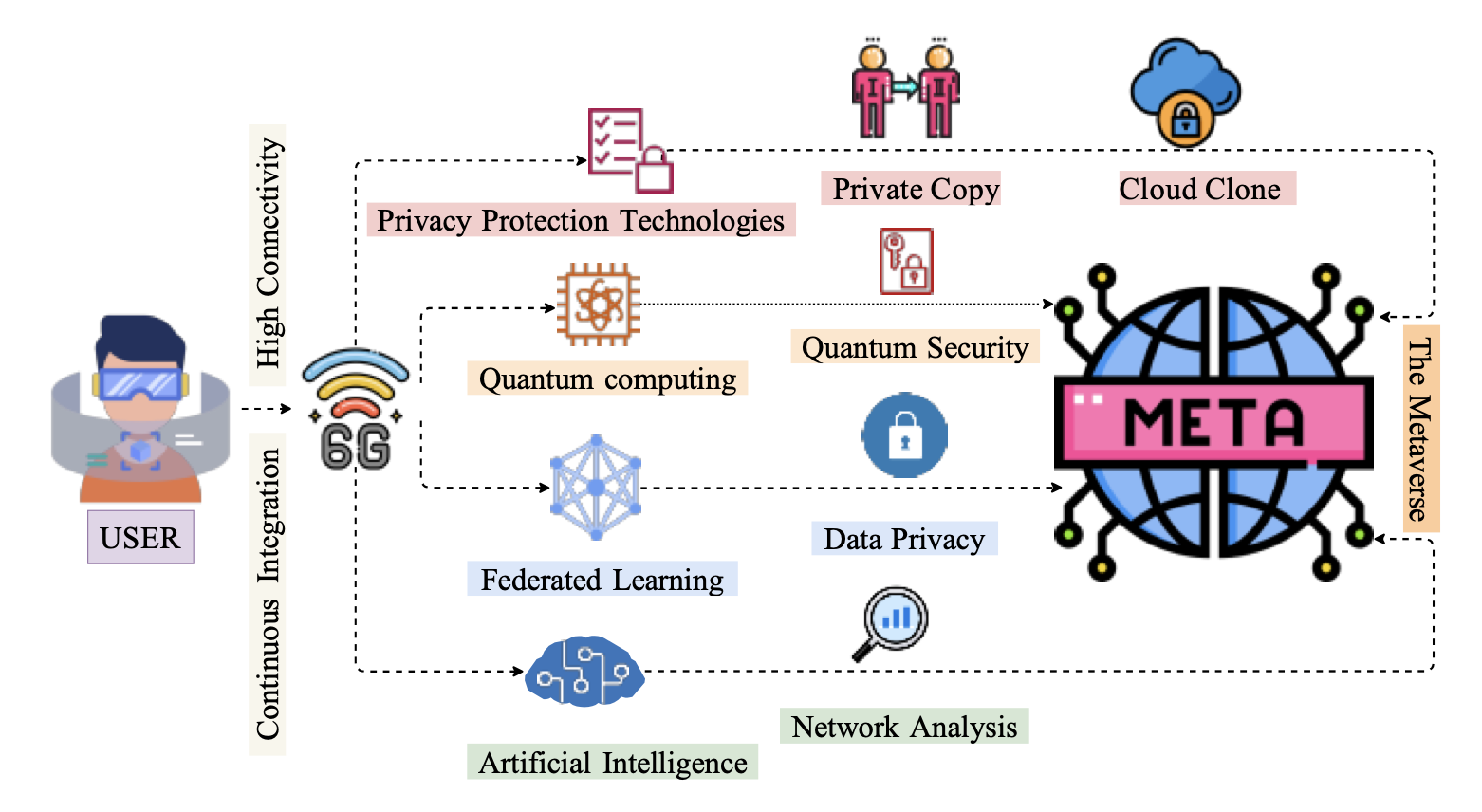
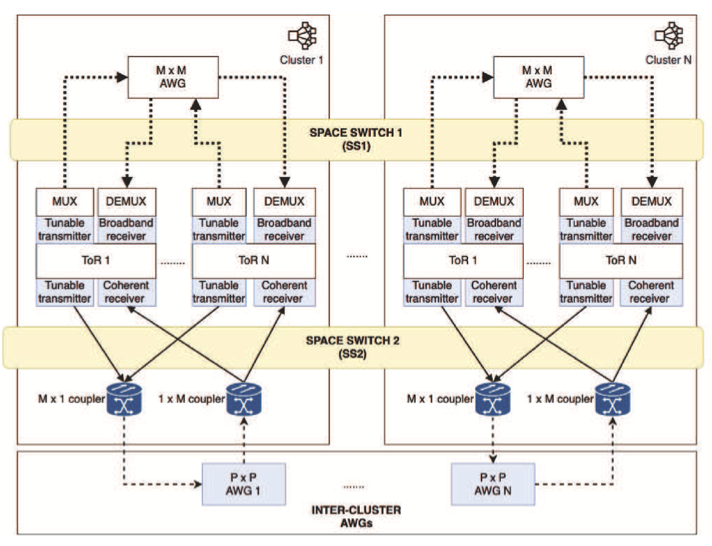
Energy blockchain applications are becoming inevitable with the transformation of electricity distributionnetworks into the decentralized Smart Grid 2.0 architecture. The scalability of the blockchain platform plays a key role in catering to the increasing number of nodes connected due to consumerturned-prosumers being integrated into the distribution grid in a distributed manner. Hence, this study aims […]
Read MoreA Novel Authentication Protocol for 5G gNodeBs in Service Migration Scenarios of MEC
- January 30, 2025
- No Comment
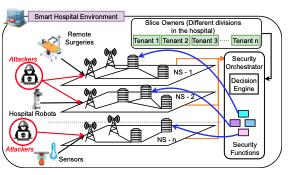
Edge computing paradigms were an expedient innovation for elevating the contemporary standards of mobile and Internet networks. As specified in Multi-Access Edge Computing (MEC) standardization, edge computing serviceable infrastructures are running on virtualization technologies to provide dynamic and flexible service instances. Since the inception and operation of the services are executing at the edge level […]
Read More